Most organizations right this moment have invested in an e-mail safety resolution of some description. However even essentially the most premium instruments have vital limitations with regards to trendy phishing assaults.
The information speaks for itself — phishing stays as large an issue because it ever was (if not larger!) regardless of monumental funding in safety merchandise and coaching. In 2024, identity-based assault vectors involving a human aspect (phishing and stolen credentials) accounted for 80% of the preliminary entry noticed by Verizon, whereas 69% of organizations skilled a phishing incident in 2024 in response to IDSA.
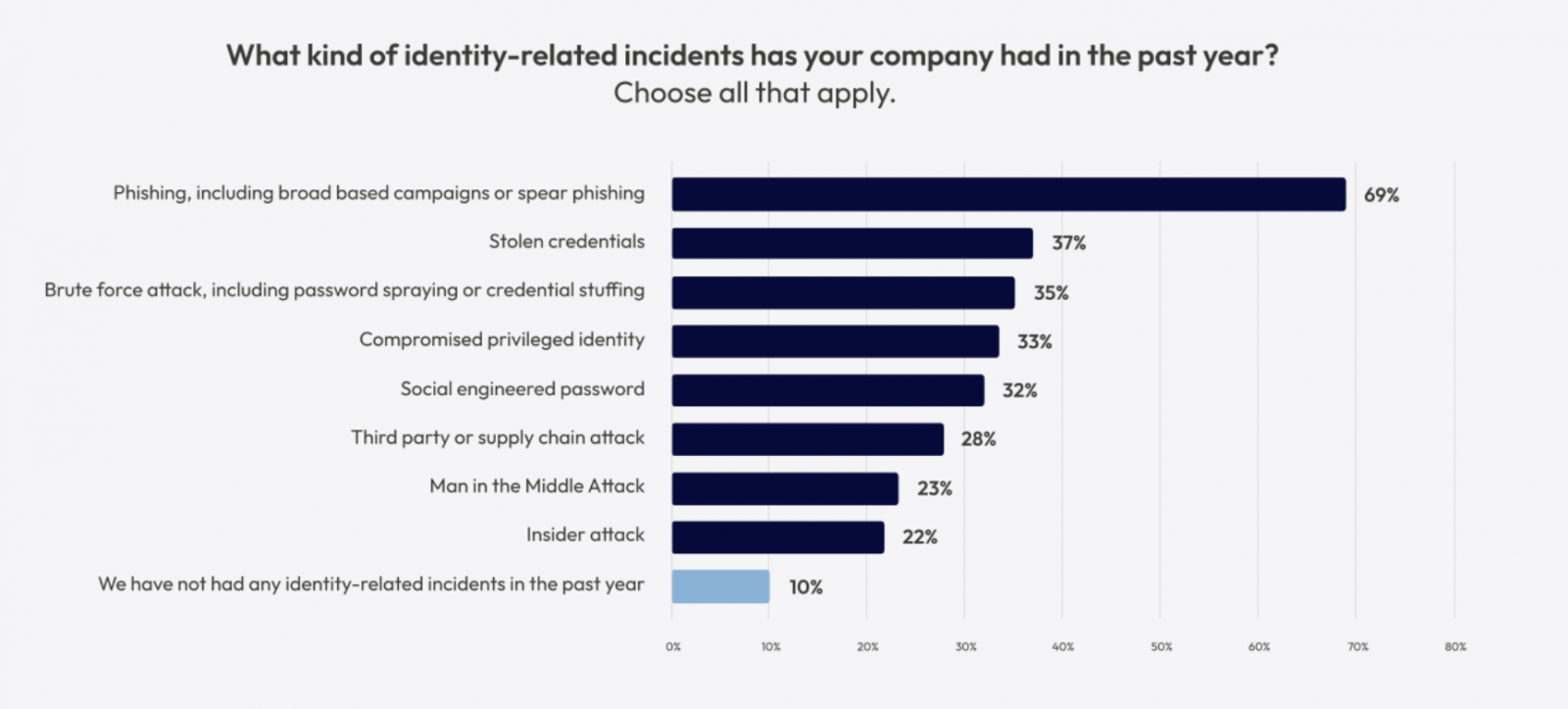
Supply: IDSA
So, why are phishing assaults nonetheless so efficient for attackers?
Trendy phishing assaults are evading established controls
Let’s begin with the lay of the land: What controls and capabilities do organizations sometimes depend on with regards to blocking credential phishing?
If you happen to’re utilizing an e-mail safety resolution, you’re counting on the next core capabilities with regards to detecting malicious phishing pages:
-
Identified-bad blocklists: Block customers from accessing known-bad or unapproved domains/URLs, and block visitors from known-bad malicious IPs, utilizing Risk Intelligence (TI) feeds.
-
Malicious webpage detection: Examine webpages by loading them in a sandbox to detect malicious components.
This additionally applies to different options that depend on these capabilities, similar to web-based content material filtering (e.g. Google Secure Shopping), CASB, SASE, SWG, and so on.
However, attackers are actually utilizing particular techniques, methods, procedures (TTPs) and tooling designed to defeat these options.
Let’s have a look at the place these controls are falling quick.
The overwhelming majority of phishing assaults right this moment are executed utilizing AitM phishing kits — in any other case referred to as “MFA bypass” kits.
These kits use devoted tooling to behave as a proxy between the goal and a official login portal for an software. This enables the goal to log in efficiently with a official service they use and even proceed to work together with it.
Because it’s a proxy to the actual software, the web page will seem precisely because the person expects, as a result of they’re logging into the official web site – simply taking a detour by way of the attacker’s machine.
Nonetheless, as a result of the attacker is sitting in the course of this connection, they’re able to observe all interactions, intercept authentication materials like credentials, MFA codes, and session tokens to take management of the authenticated session and achieve management of the person account.
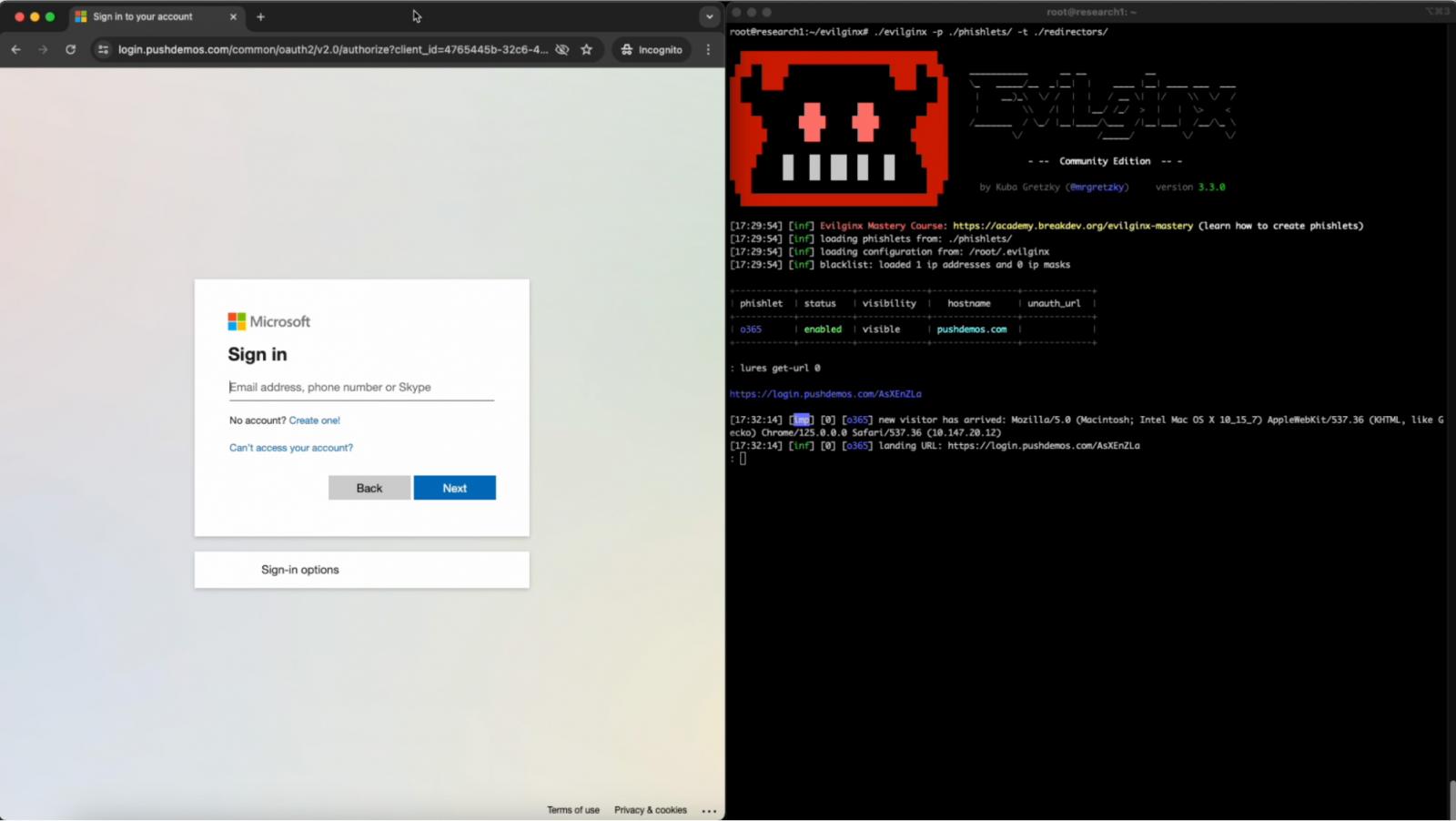
Supply: Push Safety
MFA was as soon as extensively thought to be the silver bullet for phishing (all of us bear in mind the Microsoft stat “MFA prevents over 99% of identity-based assaults”) however that is now not the case.
Not solely are these kits extremely efficient at bypassing different anti-phishing controls like MFA, attackers are constructing them particularly to evade frequent detection tooling and methods.
Guide a demo to see how Push’s browser-based identification safety platform prevents account takeover assaults like MFA-bypass phishing, credential stuffing, password spraying, and session hijacking.
Discover, repair, and defend workforce identities the place they’re created and used — in worker browsers.
Identified-bad blocklists can’t sustain
The elemental limitation with known-bad blocklists is that they concentrate on indicators which can be straightforward for attackers to alter, in flip making detections primarily based on them straightforward to bypass.
Attackers have gotten fairly good at disguising and rotating these components. In trendy phishing assaults, each goal can obtain a novel e-mail and hyperlink. Even simply utilizing a URL shortener can bypass this. It’s equal to a malware hash – trivial to alter, and subsequently not a fantastic factor to pin your detections on. The type of detection that sits proper on the backside of the Pyramid of Ache.
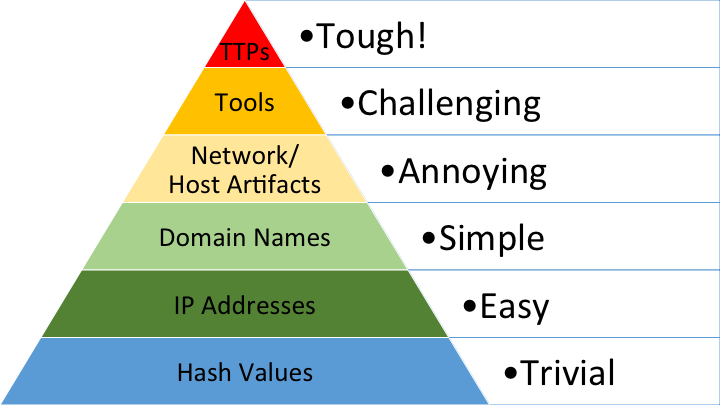
You can have a look at which IP deal with the person connects to, however lately it’s quite simple for attackers so as to add a brand new IP to their cloud-hosted server. If a website is flagged as known-bad, the attacker solely has to register a brand new area, or compromise a WordPress server on an already trusted area.
Each of these items are occurring on a large scale as attackers pre-plan for the truth that their domains can be burned sooner or later. Attackers are more than pleased to spend $10-$20 per new area within the grand scheme of the potential proceeds of crime.
For instance, latest examples of Adversary-in-the-Center phishing kits together with Tycoon, Nakedpages, Evilginx have been seen to rotate the URLs they resolve to (from a regularly refreshed pool of URLs), masks the HTTP Referer header to disguise suspicious redirects, and redirect to benign (official) domains if anybody however the meant victims tried to go to the web page.
And in lots of instances, attackers are leveraging official SaaS providers to conduct their campaigns (typically even utilizing e-mail safety providers themselves!) making it even tougher to filter real from dangerous hyperlinks.
However there’s a much bigger challenge right here – for defenders to know {that a} URL, IP, or area identify is dangerous, it must be reported first. When are issues reported? Sometimes after being utilized in an assault — so sadly, somebody at all times will get damage.
Malicious webpage detections are failing
Attackers are utilizing numerous methods to forestall safety instruments and bots from reaching their phishing pages to analyse them.
Utilizing official providers to host their domains is more and more frequent, with providers like Cloudflare Staff used for the preliminary gateway, and Cloudflare Turnstile to forestall safety bots from advancing to the web page.
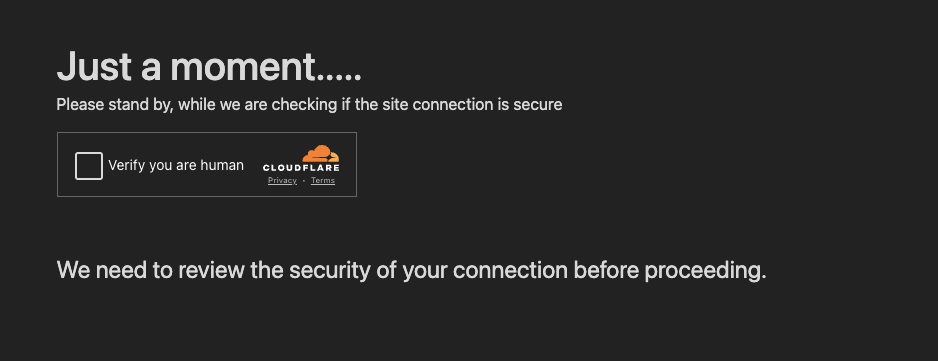
Even when you will get previous Turnstile, then you definately’ll want to provide the right URL parameters and headers, and execute JavaScript, to be served the malicious web page. Which means a defender who is aware of the area identify can’t uncover the malicious habits simply by making a easy HTTP(S) request to the area.
And if all this wasn’t sufficient, they’re additionally obfuscating each visible and DOM components to forestall signature-based detections from selecting them up — so even if you happen to can land on the web page, there’s a excessive probability that your detections gained’t set off.
By altering the DOM construction, attackers are loading functionally equal pages that look very totally different underneath the hood.
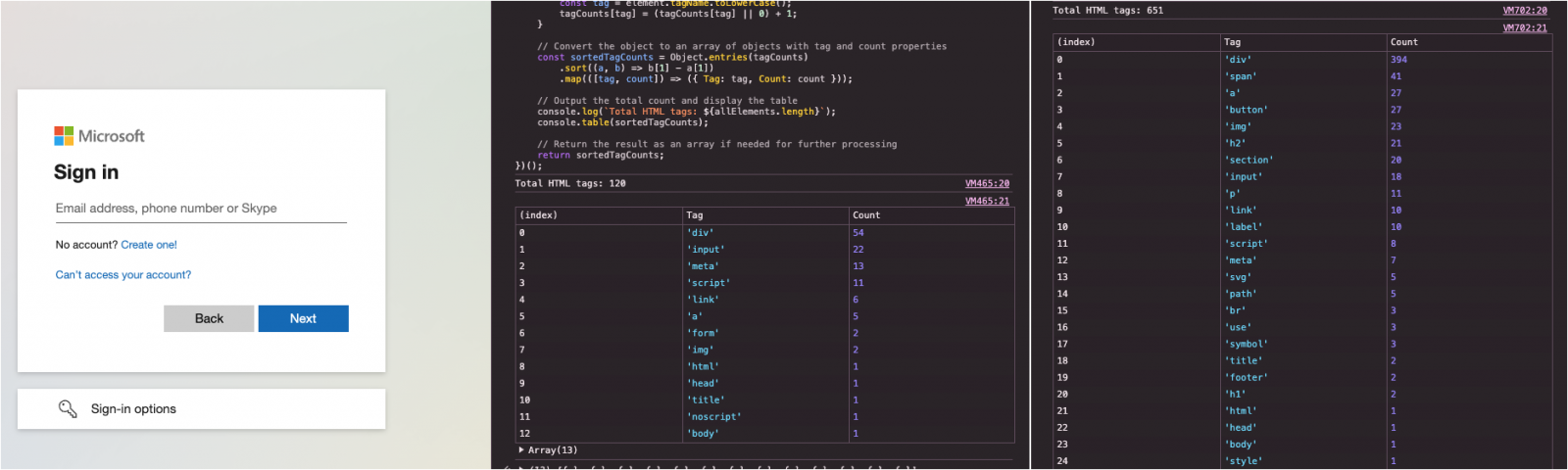
Supply: Push Safety
They’re additionally randomizing web page titles, dynamically decoding textual content, altering the dimensions and identify of picture components, utilizing totally different favicons, blurring backgrounds, substituting logos, and extra… all to defeat frequent detections.
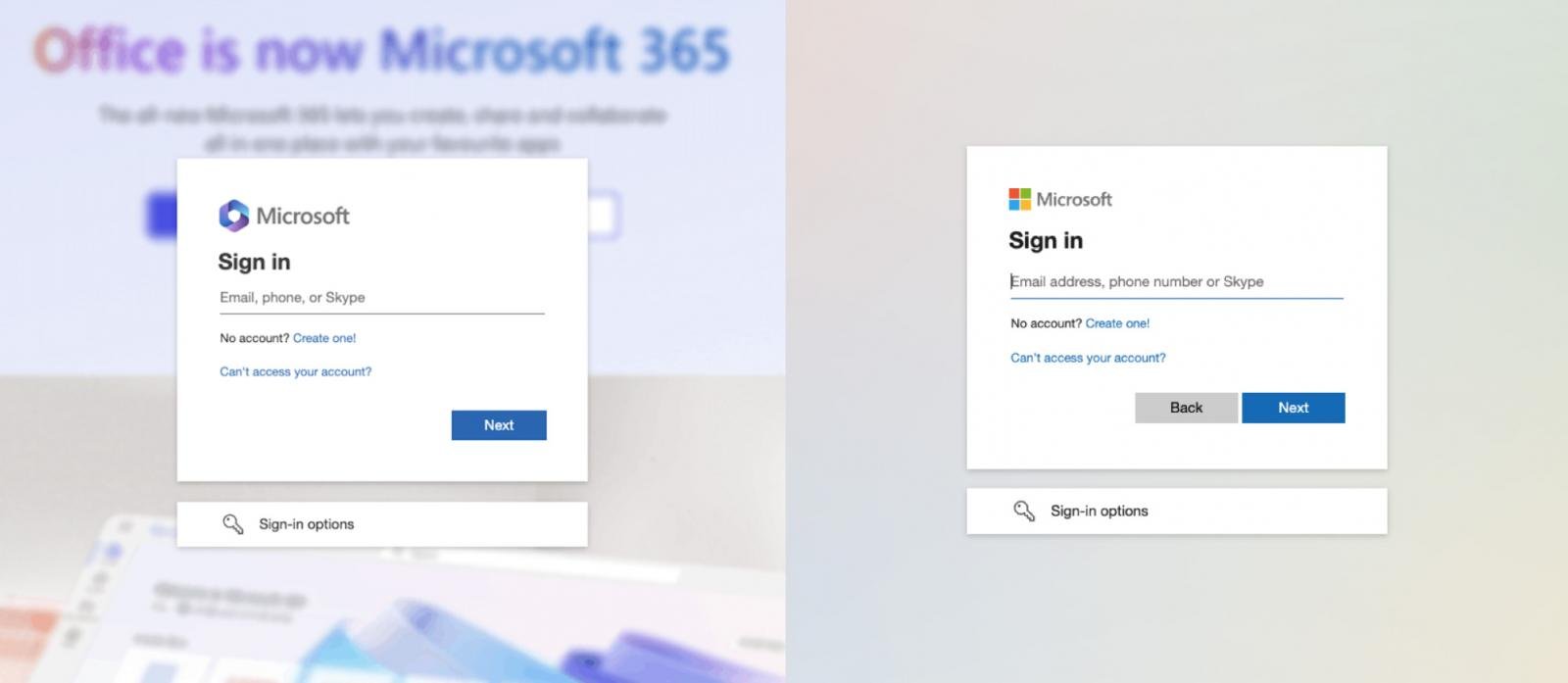
Supply: Push Safety
With all this, it’s no shock that defenders can’t sustain.
Traditionally, the trade has seen e-mail safety options and anti-phishing as the identical factor. Nevertheless it’s clear that email-based phishing safety isn’t actually reducing it with regards to trendy credential phishing assaults (the most typical and impactful phishing variant right this moment).
This isn’t to say that email-based options don’t have any worth — removed from it. However counting on e-mail scanners to detect phishing pages as a single line of protection isn’t sufficient anymore.
The important thing to fixing this downside is, put merely, constructing higher controls. However to do that, we have to transfer away from e-mail as being the first (or typically the one) place the place phishing assaults might be stopped.
Whereas e-mail is the primary supply vector for phishing assaults (no less than, in response to the info we have now, which comes primarily from e-mail safety options) it’s not the one one. Phishing hyperlinks are more and more delivered to victims over IM platforms, social media — and usually over the web.
A greater resolution to the issue would subsequently be capable of observe the person throughout the websites they use, and see the precise phishing pages because the person sees them, versus a sandbox (which, as we’ve mentioned, attackers are effectively ready for).
Is browser-based phishing safety the answer?
Whereas we’ve been conditioned to consider phishing as one thing that occurs over e-mail, it’s truly the browser the place a lot of the motion occurs, whatever the preliminary supply channel.
And whereas it’s tempting to view the supply of a phishing hyperlink because the assault itself, the phish can’t succeed except the sufferer enters their real credentials on the malicious web page.
Push Safety gives a browser-based identification safety resolution that stops phishing assaults the place they occur — in worker browsers.
Being within the browser delivers a number of benefits with regards to detecting and intercepting phishing assaults. You see the reside webpage that the person sees, that means you will have a lot better visibility of malicious components working on the web page. It additionally means which you could implement real-time controls that kick in when a malicious aspect is detected.
There’s a transparent distinction while you examine a phishing assault with and with out Push.
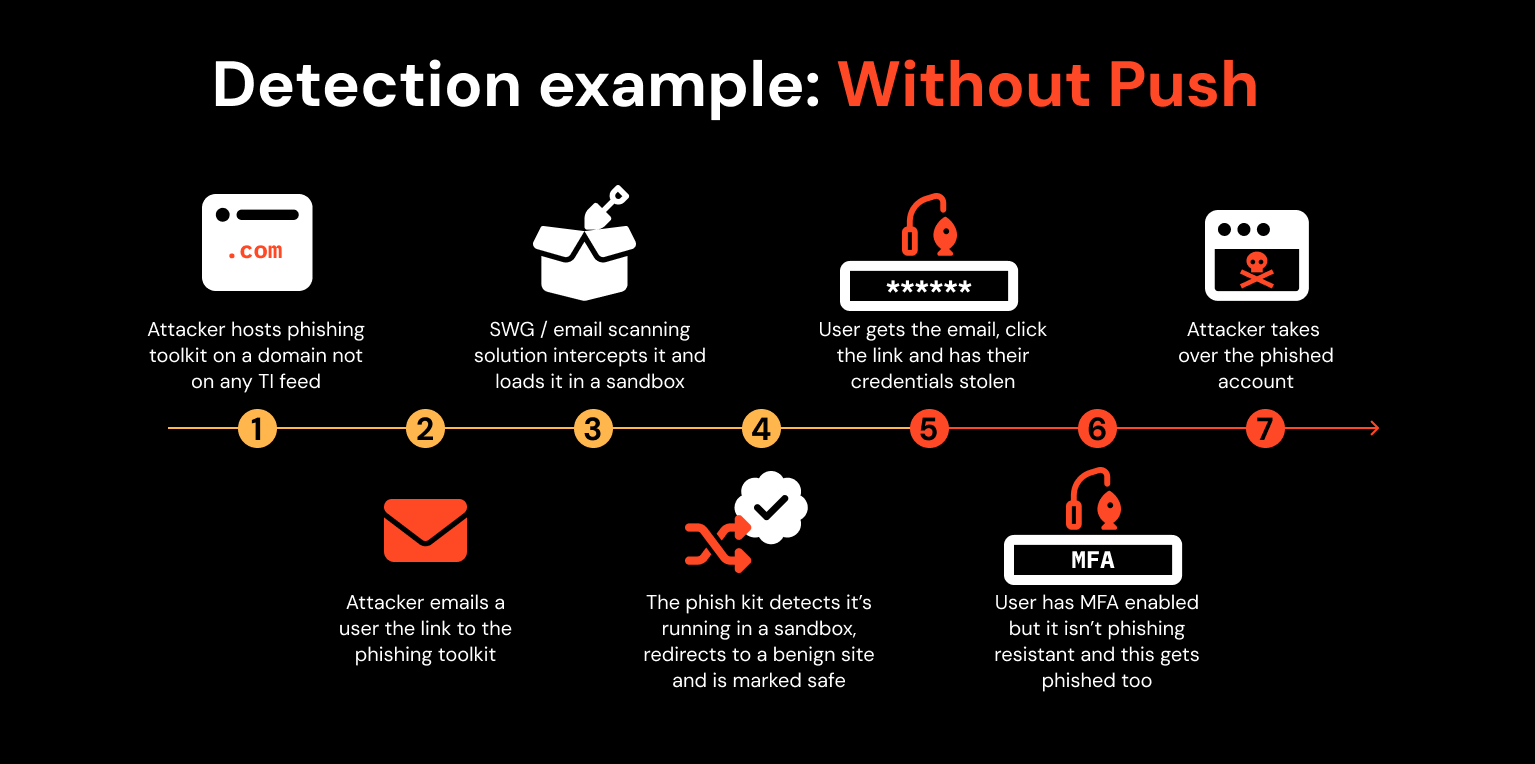
Right here, an attacker hacks a WordPress weblog to get a good area after which runs a phishing toolkit on the webpage. They e-mail one among your workers a hyperlink to it. Your SWG or e-mail scanning resolution inspects it in a sandbox however the phish equipment detects this and redirects to a benign web site in order that it passes the inspection.
Your person will get the e-mail with the hyperlink and is now free to work together with the phishing web page. They enter their credentials plus MFA code into the web page and voila! The attacker steals the authenticated session and takes over the person’s account.
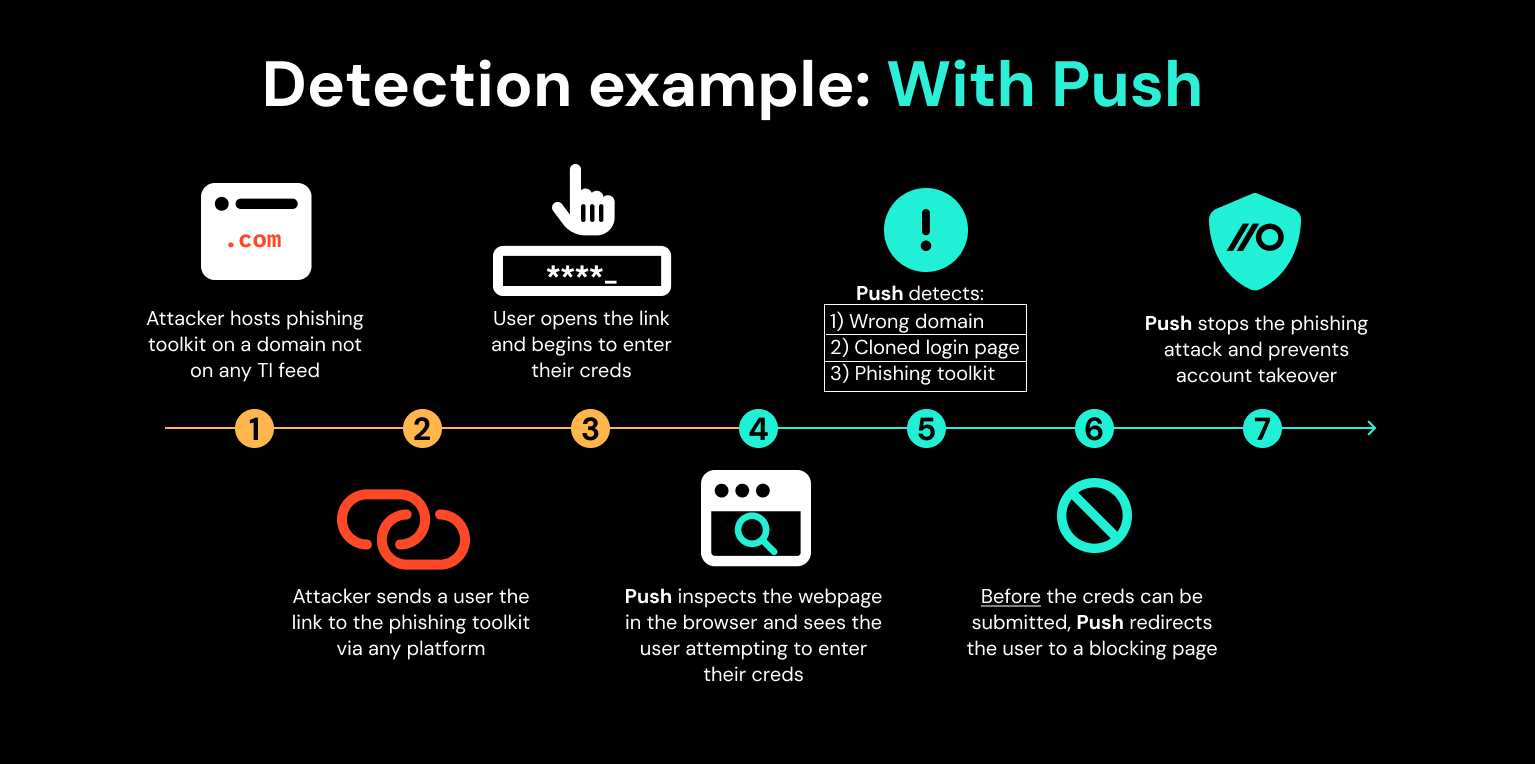
However with Push, the Push browser extension inspects the webpage working within the person’s browser. Push observes that the webpage is a login web page and the person is coming into their password into the web page, detecting that:
-
The password the person is coming into matches the area that password is pinned to. Because it does not match, primarily based on this detection alone the person is robotically redirected to a blocking web page.
-
The rendered internet app is utilizing a cloned app login web page.
-
A phishing toolkit is working on the internet web page.
Because of this, the person is blocked from interacting with the phishing web site and prevented from persevering with.
These are good examples of detections which can be troublesome (or inconceivable) for an attacker to evade — you may’t phish a sufferer if they’ll’t enter their credentials into your phishing web site!
If we have a look at the Pyramid of Ache once more, we will see that these are a lot tougher detections for attackers to get round, enabling earlier detection and interception of account takeover when in comparison with static, TI-driven blocklists — stopping assaults earlier than anybody will get damage.
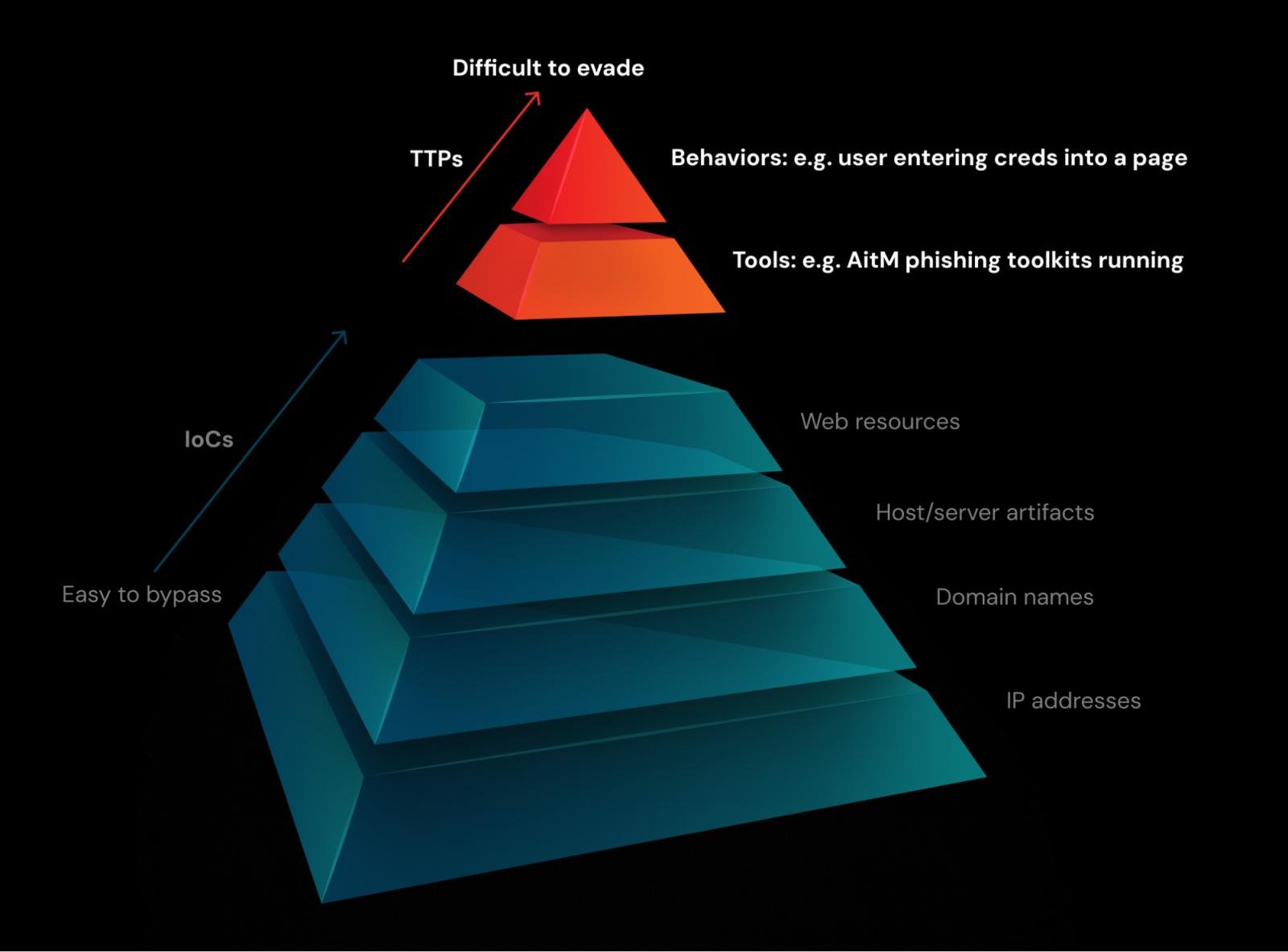
Supply: Push Safety
Try it out for your self
You’ll be able to attempt a few of our anti-phishing controls free of charge. Enroll by hitting the ‘login’ button and making a free account. Simply observe the directions right here to get began.
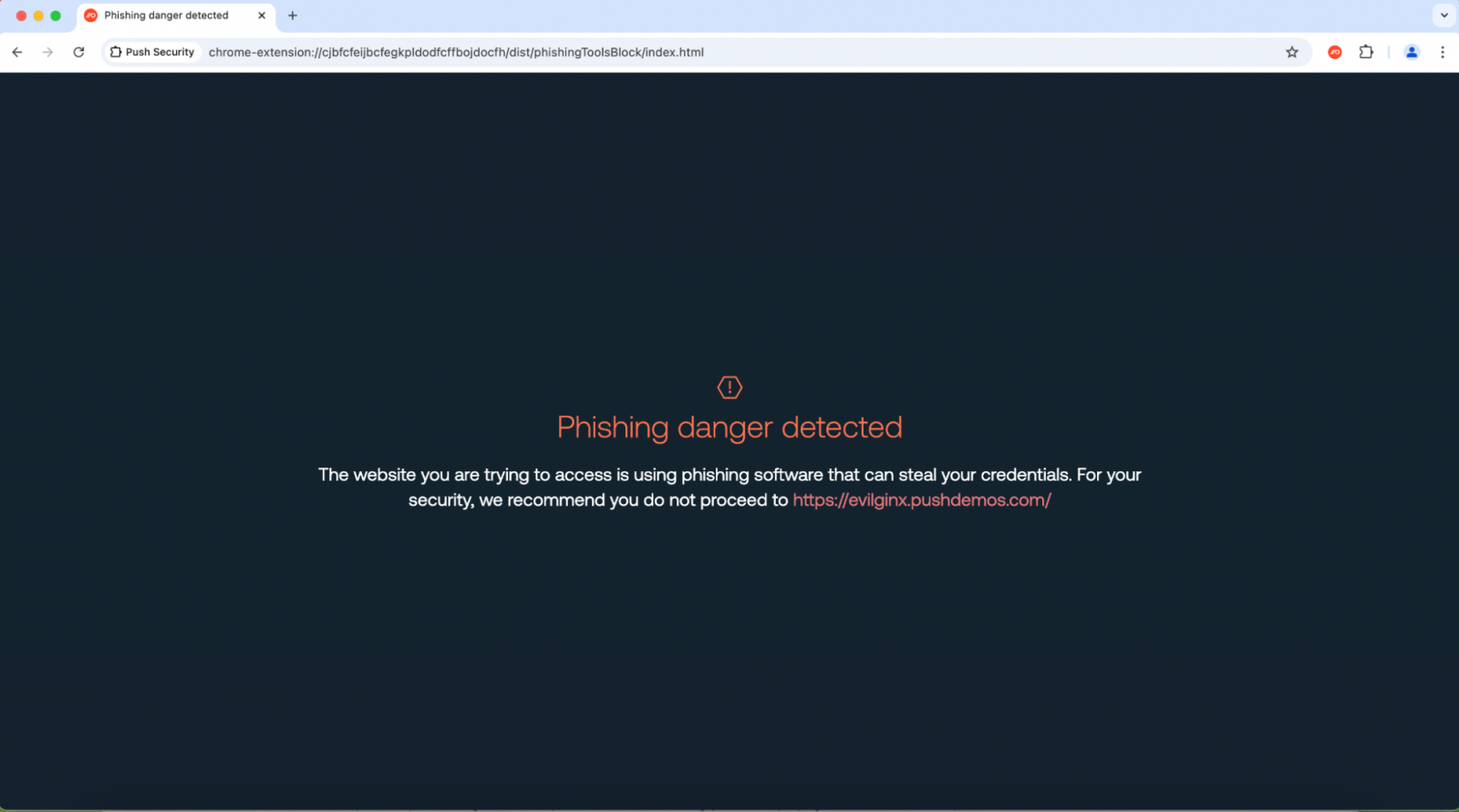
Supply: Push Safety
We don’t simply cease phishing assaults
It doesn’t cease there — Push gives complete identification assault detection and response capabilities in opposition to methods like credential stuffing, password spraying and session hijacking utilizing stolen session tokens. It’s also possible to use Push to search out and repair identification vulnerabilities throughout each app that your workers use like: ghost logins; SSO protection gaps; MFA gaps; weak, breached and reused passwords; dangerous OAuth integrations; and extra.
If you wish to be taught extra about how Push lets you detect and defeat frequent identification assault methods, ebook a while with one among our crew for a reside demo.
Sponsored and written by Push Safety.

