
The ShinyHunters extortion gang claims it’s behind a wave of ongoing voice phishing assaults concentrating on single sign-on (SSO) accounts at Okta, Microsoft, and Google, enabling menace actors to breach company SaaS platforms and steal firm knowledge for extortion.
In these assaults, menace actors impersonate IT assist and name staff, tricking them into getting into their credentials and multi-factor authentication (MFA) codes on phishing websites that impersonate firm login portals.
As soon as compromised, the attackers acquire entry to the sufferer’s SSO account, which might present entry to different related enterprise functions and companies.
SSO companies from Okta, Microsoft Entra, and Google allow corporations to hyperlink third-party functions right into a single authentication circulation, giving staff entry to cloud companies, inner instruments, and enterprise platforms with a single login.
These SSO dashboards sometimes listing all related companies, making a compromised account a gateway into company methods and knowledge.
Platforms generally related via SSO embody Salesforce, Microsoft 365, Google Workspace, Dropbox, Adobe, SAP, Slack, Zendesk, Atlassian, and plenty of others.

Supply: Microsoft
Vishing assaults used for knowledge theft
As first reported by BleepingComputer, menace actors have been finishing up these assaults by calling staff and posing as IT workers, utilizing social engineering to persuade them to log into phishing pages and full MFA challenges in actual time.
After having access to a sufferer’s SSO account, the attackers browse the listing of related functions and start harvesting knowledge from the platforms accessible to that person.
BleepingComputer is conscious of a number of corporations focused in these assaults which have since obtained extortion calls for signed by ShinyHunters, indicating that the group was behind the intrusions.
BleepingComputer contacted Okta earlier this week in regards to the breaches, however the firm declined to touch upon the information theft assaults.
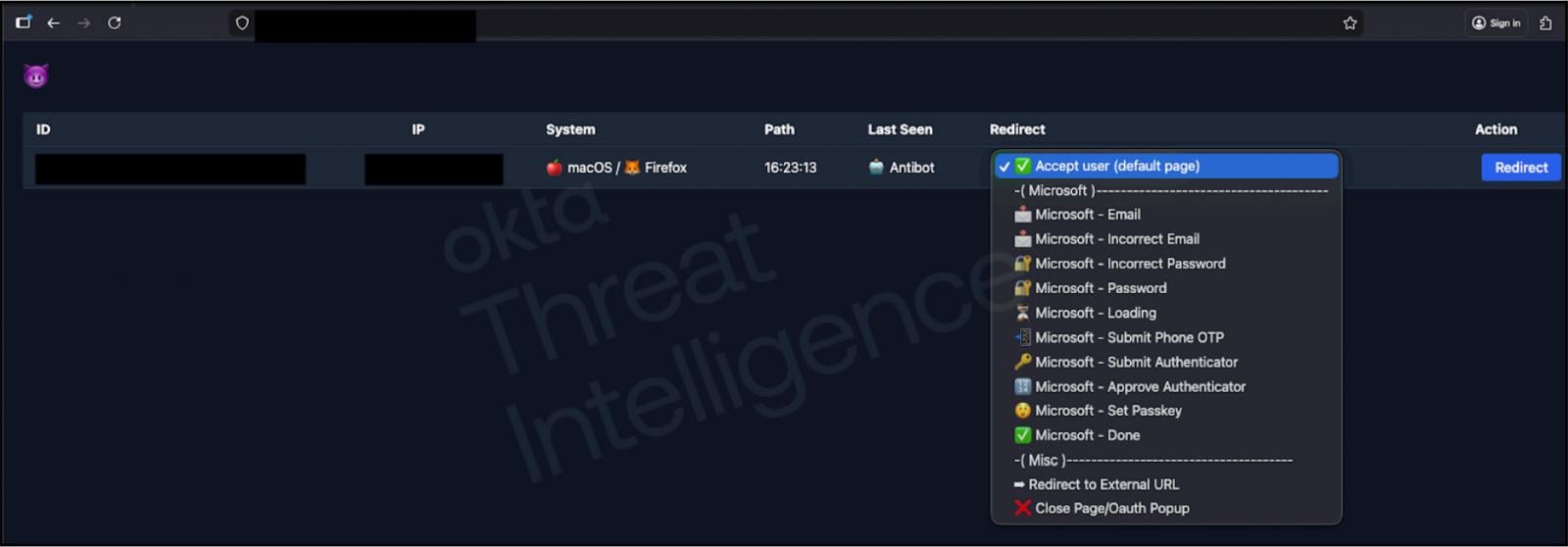
Nevertheless, Okta launched a report yesterday describing the phishing kits utilized in these voice-based assaults, which match what BleepingComputer has been informed.
In accordance with Okta, the phishing kits embody a web-based management panel that enables attackers to dynamically change what a sufferer sees on a phishing website whereas chatting with them on the telephone. This enables menace actors to information victims via every step of the login and MFA authentication course of.
If the attackers enter stolen credentials into the actual service and are prompted for MFA, they’ll show new dialog packing containers on the phishing website in actual time to instruct a sufferer to approve a push notification, enter a TOTP code, or carry out different authentication steps.
Supply: Okta
ShinyHunters declare duty
Whereas ShinyHunters declined to touch upon the assaults final evening, the group confirmed to BleepingComputer this morning that it’s liable for a number of the social engineering assaults.
“We affirm we’re behind the assaults,” ShinyHunters informed BleepingComputer. “We’re unable to share additional particulars presently, moreover the truth that Salesforce stays our major curiosity and goal, the remainder are benefactors.”
The group additionally confirmed different elements of BleepingComputer’s reporting, together with particulars in regards to the phishing infrastructure and domains used within the marketing campaign. Nevertheless, it disputed {that a} screenshot of a phishing package command-and-control server shared by Okta was for its platform, claiming as a substitute that theirs was constructed in-house.
ShinyHunters claimed it’s concentrating on not solely Okta but in addition Microsoft Entra and Google SSO platforms.
Microsoft mentioned it has nothing to share presently, and Google mentioned it had no proof its merchandise had been being abused within the marketing campaign.
“Right now, we have now no indication that Google itself or its merchandise are affected by this marketing campaign,” a Google spokesperson informed BleepingComputer.
ShinyHunters claims to be utilizing knowledge stolen in earlier breaches, such because the widespread Salesforce knowledge theft assaults, to determine and get in touch with staff. This knowledge contains telephone numbers, job titles, names, and different particulars used to make the social-engineering calls extra convincing.
Final evening, the group relaunched its Tor knowledge leak website, which presently lists breaches at SoundCloud, Betterment, and Crunchbase.
SoundCloud beforehand disclosed an information breach in December 2025, whereas Betterment confirmed this month that its electronic mail platform had been abused to ship cryptocurrency scams and that knowledge was stolen.
Crunchbase, which had not beforehand disclosed a breach, confirmed as we speak that knowledge was stolen from its company community.
“Crunchbase detected a cybersecurity incident the place a menace actor exfiltrated sure paperwork from our company community,” an organization spokesperson informed BleepingComputer. “No enterprise operations have been disrupted by this incident. We’ve got contained the incident and our methods are safe.”
“Upon detecting the incident we engaged cybersecurity consultants and contacted federal regulation enforcement. We’re reviewing the impacted info to find out if any notifications are required per relevant authorized necessities.”
It is price range season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the yr forward. This report compiles their insights, permitting readers to benchmark methods, determine rising tendencies, and examine their priorities as they head into 2026.
Find out how prime leaders are turning funding into measurable impression.



