
Over 77,000 Web-exposed IP addresses are susceptible to the essential React2Shell distant code execution flaw (CVE-2025-55182), with researchers now confirming that attackers have already compromised over 30 organizations throughout a number of sectors.
React2Shell is an unauthenticated distant code execution vulnerability that may be exploited by way of a single HTTP request and impacts all frameworks that implement React Server Elements, together with Subsequent.js, which makes use of the identical deserialization logic.
React disclosed the vulnerability on December 3, explaining that unsafe deserialization of client-controlled information inside React Server Elements permits attackers to set off distant, unauthenticated execution of arbitrary instructions.
Builders are required to replace React to the most recent model, rebuild their functions, after which redeploy to repair the vulnerability.
On December 4, safety researcher Maple3142 revealed a working proof-of-concept demonstrating distant command execution towards unpatched servers. Quickly after, scanning for the flaw accelerated as attackers and researchers started utilizing the general public exploit with automated instruments.
Over 77,000 susceptible IP addresses
Shadowserver Web watchdog group now reviews that it has detected 77,664 IP addresses susceptible to the React2Shell flaw, with roughly 23,700 in the US.
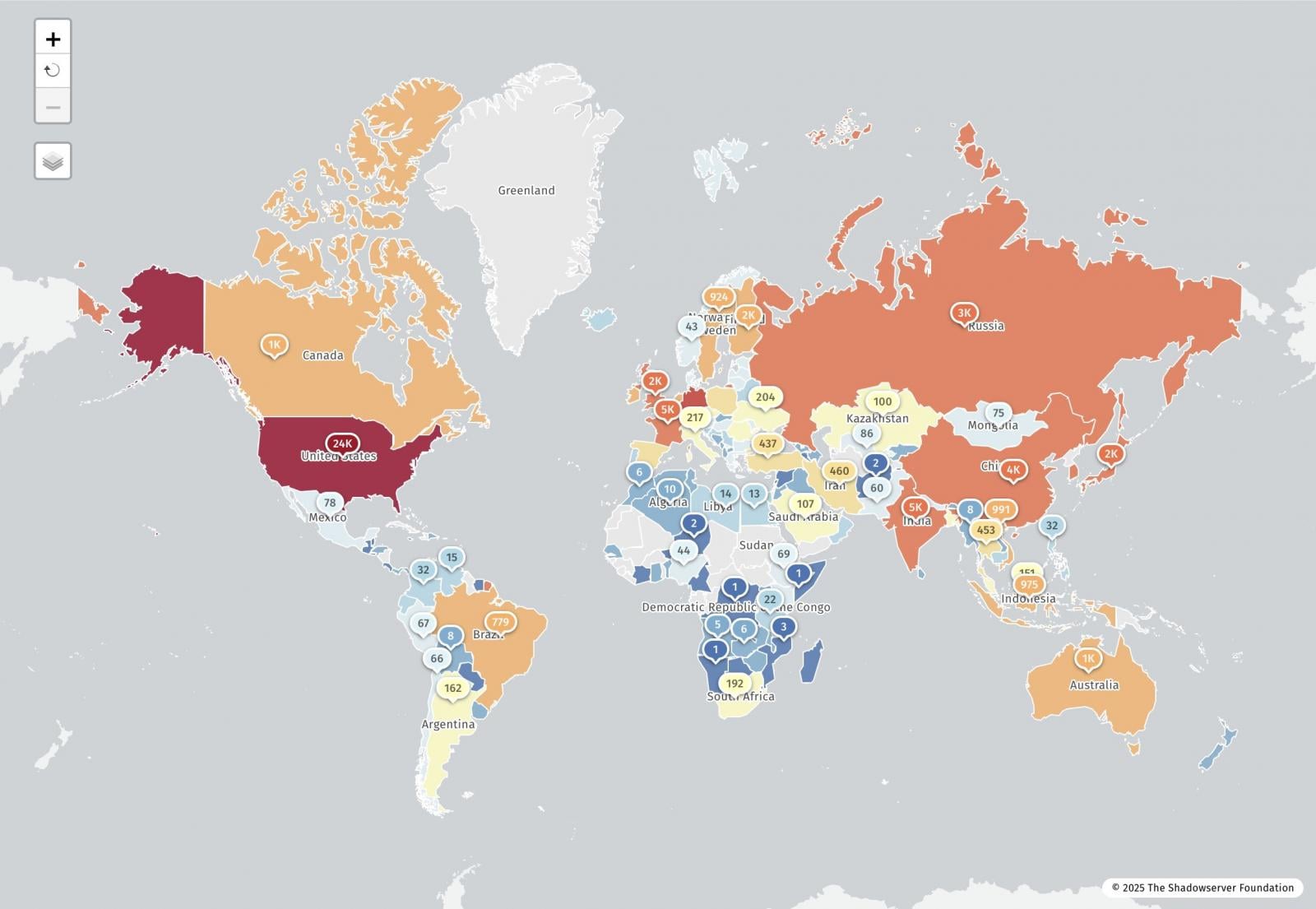
Supply: ShadowServer
The researchers decided that IP addresses have been susceptible utilizing a detection method developed by Searchlight Cyber/Assetnote, the place an HTTP request was despatched to servers to use the flaw, and a particular response was checked to verify whether or not a tool was susceptible.
GreyNoise additionally recorded 181 distinct IP addresses making an attempt to use the flaw over the previous 24 hours, with a lot of the site visitors showing automated. The researchers say the scans are primarily originating from the Netherlands, China, the US, Hong Kong, and a small variety of different nations.
Supply: Greynoise
Palo Alto Networks reviews that greater than 30 organizations have already been compromised by way of the React2Shell flaw, with attackers exploiting the vulnerability to run instructions, conduct reconnaissance, and try to steal AWS configuration and credential information.
These compromises embody intrusions linked to recognized state-associated Chinese language menace actors.
Widespread exploitation of React2Shell
Since its disclosure, researchers and menace intelligence firms have noticed widespread exploitation of the CVE-2025-55182 flaw.
GreyNoise reviews that attackers incessantly start with PowerShell instructions that carry out a primary math perform to verify the gadget is susceptible to the distant code execution flaw.
These exams return predictable outcomes whereas leaving minimal indicators of exploitation:
powershell -c "40138*41979"
powershell -c "40320*43488"
As soon as distant code execution was confirmed, attackers have been seen executing base64-encoded PowerShell instructions that obtain extra scripts immediately into reminiscence.
powershell -enc
One noticed command executes a second-stage PowerShell script from the exterior web site (23[.]235[.]188[.]3), which is used to disable AMSI to bypass endpoint safety and deploy extra payloads.
In keeping with VirusTotal, the PowerShell script noticed by GreyNoise installs a Cobalt Strike beacon on the focused gadget, giving menace actors a foothold on the community.
Amazon AWS menace intelligence groups additionally noticed fast exploitation hours after the disclosure of the React CVE-2025-55182 flaw, with infrastructure related to China-linked APT hacking teams often known as Earth Lamia and Jackpot Panda.
On this exploitation, the menace actors carry out reconnaissance on susceptible servers by utilizing instructions corresponding to whoami and id, making an attempt to jot down information, and studying /and many others/passwd.
Palo Alto Networks additionally noticed related exploitation, attributing a few of it to UNC5174, a Chinese language state-sponsored menace actor believed to be tied to the Chinese language Ministry of State Safety.
“Unit 42 noticed menace exercise we assess with excessive confidence is in step with CL-STA-1015 (aka UNC5174), a gaggle suspected to be an preliminary entry dealer with ties to the Chinese language Ministry of State Safety,” Justin Moore, Senior Supervisor at Palo Alto Networks Unit 42, advised BleepingComputer by way of electronic mail.
“On this exercise, we noticed the deployment of Snowlight and Vshell malware, each extremely in step with Unit 42 information of CL-STA-1015 (also called UNC5174).”
The deployed malware in these assaults is:
- Snowlight: A malware dropper that permits distant attackers to drop extra payloads on breached units.
- Vshell: A backdoor generally utilized by Chinese language hacking teams for distant entry, post-exploitation exercise, and to maneuver laterally by way of a compromised community.
The push to patch
As a result of severity of the React flaw, firms worldwide have rushed to put in the patch and apply mitigations.
Yesterday, Cloudflare rolled out emergency detections and mitigations for the React flaw in its Net Utility Firewall (WAF) on account of its widespread exploitation and severity.
Nonetheless, the replace inadvertently prompted an outage affecting quite a few web sites earlier than the foundations have been corrected.
CISA has additionally added CVE-2025-55182 to the Identified Exploited Vulnerabilities (KEV) catalog, requiring federal companies to use patches by December 26, 2025, below Binding Operational Directive 22-01.
Organizations utilizing React Server Elements or frameworks constructed on high of them are suggested to use updates instantly, rebuild and redeploy their functions, and evaluate logs for indicators of PowerShell or shell command execution.
Damaged IAM is not simply an IT drawback – the impression ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM appears like, and a easy guidelines for constructing a scalable technique.


