
The RansomHouse ransomware-as-a-service (RaaS) has just lately upgraded its encryptor, switching from a comparatively easy single-phase linear approach to a extra complicated, multi-layered methodology.
In follow, the upgrades provide stronger encryption outcomes, quicker speeds, and higher reliability on fashionable goal environments, giving risk actors stronger leverage throughout post-encryption negotiations.
RansomHouse launched in December 2021 as a information extortion cybercrime operation, later adopting encryptors in assaults and growing an automated software known as MrAgent to lock a number of VMware ESXi hypervisors without delay.
Just lately, it was reported that the risk actors used a number of ransomware households in opposition to the Japanese e-commerce large Askul Company.
A brand new report from researchers at Palo Alto Networks Unit 42 sheds extra gentle on RansomHouse’s toolset, together with its newest encryptor variant, dubbed ‘Mario.’
New ‘Mario’ encryptor
RansomHouse’s newest encryptor variant switches from a single-pass file information transformation to a two-stage transformation that leverages two keys, a 32-byte major and an 8-byte secondary key.
This method will increase the encryption entropy and makes partial information restoration more durable.
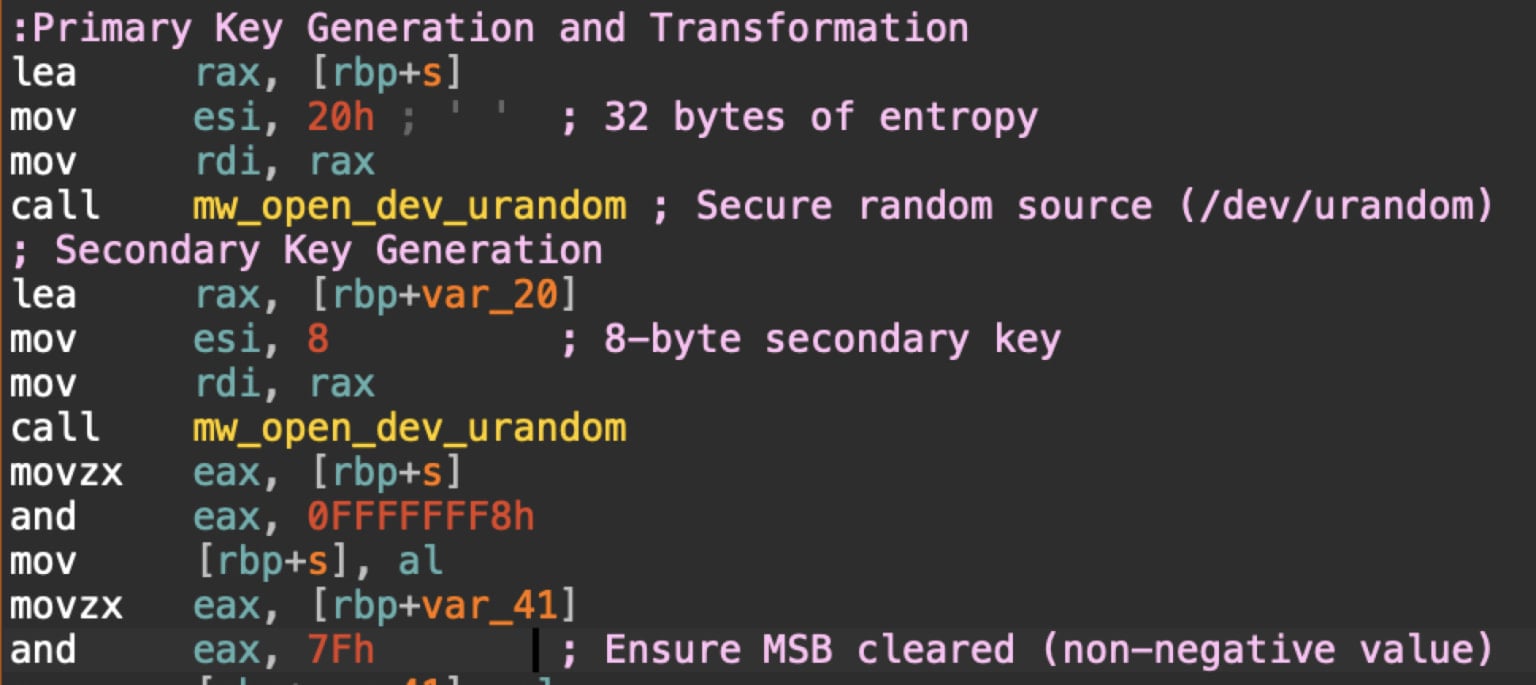
Supply: Unit 42
The second main improve is the introduction of a brand new file processing technique that makes use of dynamic chunk sizing at a threshold of 8GB, with intermittent encryption.
Unit 42 says this makes static evaluation harder resulting from its non-linearity, use of complicated math to find out the processing order, and using distinct approaches for every file primarily based on its measurement.
One other notable improve in ‘Mario’ is the higher reminiscence structure and buffer group, and better complexity, with a number of devoted buffers now used for every encryption stage or position.
Lastly, the upgraded encryptor model now prints extra detailed data for file processing in contrast with the older variants, which solely declared the duty completion.
The newer variant nonetheless targets VM information and renames the encrypted information with the ‘.emario’ extension, dropping a ransom observe (How To Restore Your Recordsdata.txt) on all impacted directories.
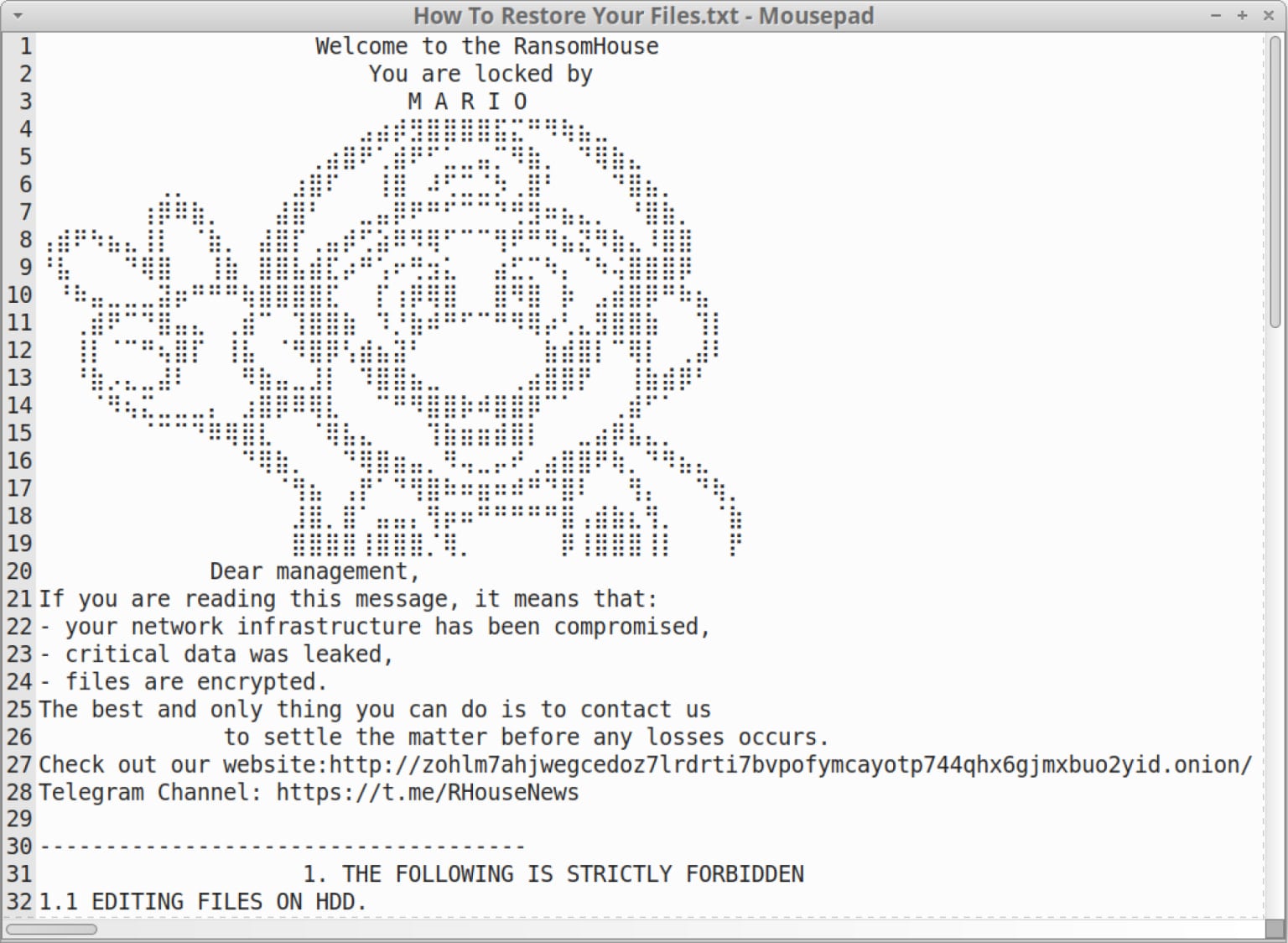
Supply: Unit 42
Unit 42 concludes that RansomHouse’s encryption improve is alarming, signaling “a regarding trajectory in ransomware improvement,” rising the issue of decryption and making static evaluation and reverse engineering more durable.
RansomHouse is without doubt one of the longer-running RaaS operations, nevertheless it stays mid-tier by way of assault quantity. Its continued improvement of superior tooling suggests a calculated technique centered on effectivity and evasion somewhat than scale.
Damaged IAM is not simply an IT downside – the affect ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM seems like, and a easy guidelines for constructing a scalable technique.



