An e mail rip-off is abusing abusing PayPal’s “Subscriptions” billing characteristic to ship legit PayPal emails that comprise pretend buy notifications embedded within the Customer support URL subject.
Over the previous couple of months, folks have reported [1, 2] receiving emails from PayPal stating, “Your computerized cost is not lively.”
The e-mail features a customer support URL subject that was in some way modified to incorporate a message stating that you just bought an costly merchandise, similar to a Sony machine, MacBook, or iPhone.
This textual content features a area identify, a message stating {that a} cost of $1,300 to $1,600 was processed (the quantity varies by e mail), and a telephone quantity to cancel or dispute the cost. The textual content is full of Unicode characters that make parts seem daring or in an uncommon font, a tactic used to attempt to evade spam filters and key phrase detection.
“http://[domain] [domain] A cost of $1346.99 has been efficiently processed. For cancel and inquiries, Contact PayPal assist at +1-805-500-6377,” reads the customer support URL within the rip-off e mail.
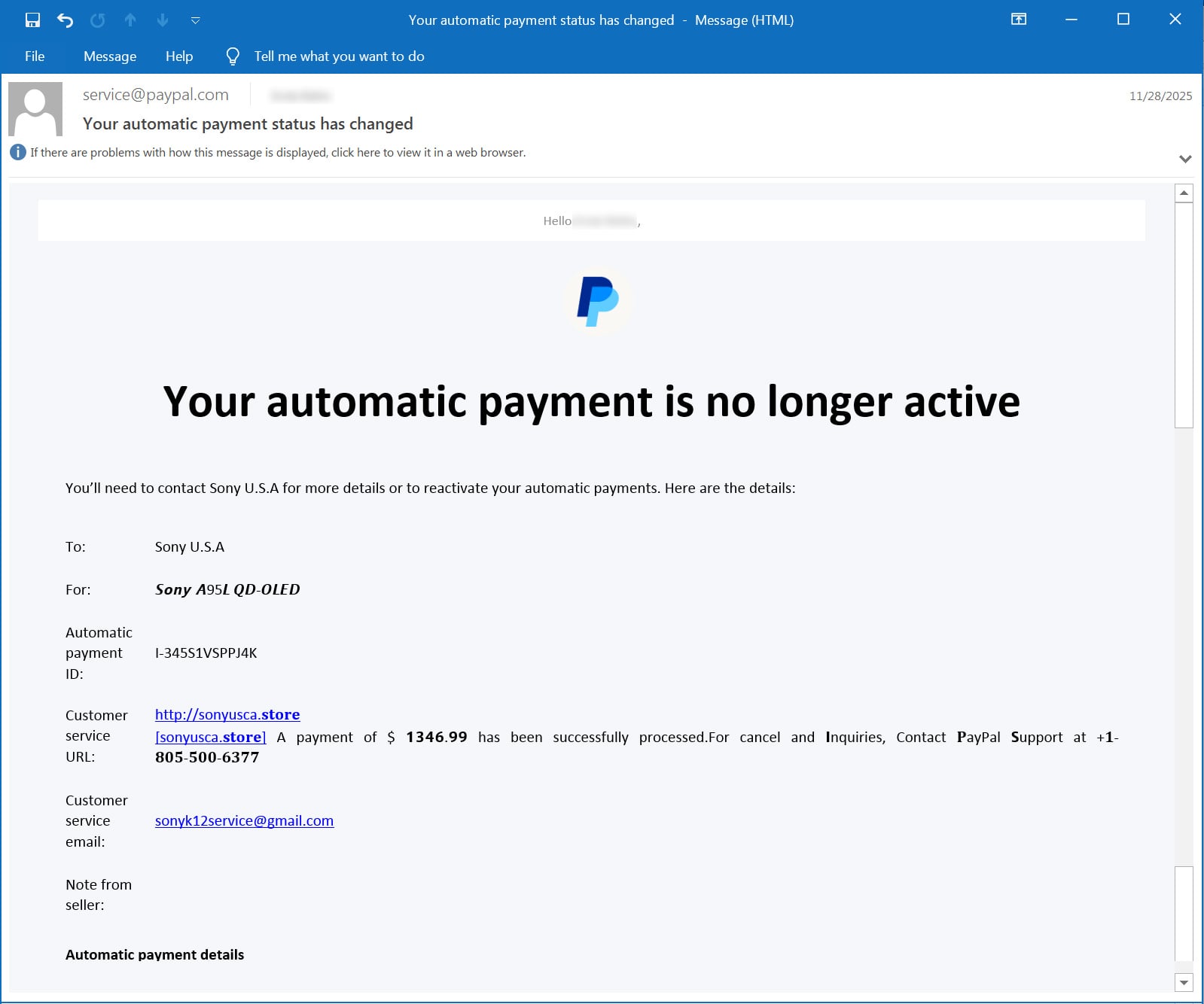
Supply: BleepingComputer
Whereas that is clearly a rip-off, the emails are being despatched instantly by PayPal from the handle “service@paypal.com,” main folks to fret their accounts might have been hacked.
Moreover, because the emails are legit PayPal emails, they’re bypassing safety and spam filters. Within the subsequent part, we are going to clarify how scammers ship these emails.
The objective of those emails is to trick recipients into pondering their account bought an costly machine and scare them into calling the scammer’s “PayPal assist” telephone quantity.
Emails like these have traditionally been used to persuade recipients to name a quantity to conduct financial institution fraud or trick them into putting in malware on their computer systems.
Subsequently, if you happen to obtain a legit e mail from PayPal stating your computerized cost is not lively, and it incorporates a pretend buy affirmation, ignore the e-mail and don’t name the quantity.
If you’re involved that your PayPal account was compromised, log in to your account and ensure that there was no cost.
How the PayPal rip-off works
BleepingComputer was despatched a replica of the e-mail from somebody who obtained it and located it unusual that the rip-off originated from the legit “service@paypal.com” e mail handle.
Moreover, the e-mail headers point out that the emails are legit, cross DKIM and SPF e mail safety checks, and originate instantly from PayPal’s “mx15.slc.paypal.com” mail server, as proven beneath.
ARC-Authentication-Outcomes: i=1; mx.google.com;
dkim=cross header.i=@paypal.com header.s=pp-dkim1 header.b="AvY/E1H+";
spf=cross (google.com: area of service@paypal.com designates 173.0.84.4 as permitted sender) smtp.mailfrom=service@paypal.com;
dmarc=cross (p=REJECT sp=REJECT dis=NONE) header.from=paypal.com
Obtained: from mx15.slc.paypal.com (mx15.slc.paypal.com. [173.0.84.4])
by mx.google.com with ESMTPS id a92af1059eb24-11dcb045a3csi5930706c88.202.2025.11.28.09.14.49
for
(model=TLS1_3 cipher=TLS_AES_256_GCM_SHA384 bits=256/256);
Fri, 28 Nov 2025 09:14:49 -0800 (PST)
After testing numerous PayPal billing options, BleepingComputer was in a position to replicate the identical e mail template by utilizing PayPal’s “Subscriptions” characteristic and pausing a subscriber.
PayPal subscriptions are a billing characteristic that lets retailers create subscription checkout choices for folks to subscribe to a service for a specified quantity.
When a service provider pauses a subscriber’s subscription, PayPal will routinely e mail the subscriber to inform them that their computerized cost is not lively.
Nevertheless, when BleepingComputer tried to duplicate the rip-off by including textual content aside from a URL to the Buyer Service URL, PayPal would reject the change as solely a URL is allowed.
Subsequently, it seems the scammers are both exploiting a flaw in PayPal’s dealing with of subscription metadata or utilizing a technique, similar to an API or legacy platform not out there in all areas, that permits invalid textual content to be saved within the Customer support URL subject.
Now that we all know how they generate the e-mail from PayPal, it is nonetheless unclear the way it’s being despatched to individuals who did not join the PayPal subscription.
The mail headers present that PayPal is definitely sending the e-mail to the handle “receipt3@bbcpaglomoonlight.studio,” which we imagine is the e-mail handle related to a pretend subscriber created by the scammer.
This account is probably going a Google Workspace mailing listing, which routinely forwards any e mail it receives to all different group members. On this case, the members are the folks the scammer is concentrating on.
This forwarding may cause all subsequent SPF and DMARC checks to fail, for the reason that e mail was forwarded by a server that was not the unique sender.
PayPal has now advised BleepingComputer that they’re mitigating the tactic used to ship these rip-off emails.
“PayPal doesn’t tolerate fraudulent exercise and we work exhausting to guard our clients from persistently evolving phishing scams,” PayPal advised BleepingComputer.
“We’re actively mitigating this matter, and encourage folks to all the time be vigilant on-line and conscious of surprising messages. If clients suspect they’re a goal of a rip-off, we suggest they contact Buyer Help instantly by means of the PayPal app or our Contact web page for help.”
Replace 12/14/25: Added up to date assertion confirming that PayPal is mitigating the tactic used to ship these emails.
Damaged IAM is not simply an IT drawback – the influence ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM seems to be like, and a easy guidelines for constructing a scalable technique.


