
Oracle is warning a few vital E-Enterprise Suite zero-day vulnerability tracked as CVE-2025-61882 that permits attackers to carry out unauthenticated distant code execution, with the flaw actively exploited in Clop information theft assaults.
The flaw is inside the Oracle Concurrent Processing product of Oracle E-Enterprise Suite (part: BI Writer Integration) and has a CVSS base rating of 9.8, attributable to its lack of authentication and ease of exploitation.
“This Safety Alert addresses vulnerability CVE-2025-61882 in Oracle E-Enterprise Suite,” reads a brand new Oracle advisory.
“This vulnerability is remotely exploitable with out authentication, i.e., it could be exploited over a community with out the necessity for a username and password. If efficiently exploited, this vulnerability might lead to distant code execution.”
Oracle has confirmed that the zero-day vulnerability impacts Oracle E-Enterprise Suite, variations 12.2.3-12.2.14, and has launched an emergency replace to deal with the flaw. The corporate notes that prospects should first set up the October 2023 Important Patch Replace earlier than they will set up the brand new safety updates.
As a public PoC exploit exists and the flaw is actively exploited, it’s essential for Oracle admins to put in the safety replace as quickly as attainable.
Zero-day exploited in Clop information theft assaults
Whereas Oracle has not explicitly said that it is a zero-day vulnerability, they did share indicators of compromise that correspond to an Oracle EBS exploit not too long ago shared by risk actors on Telegram.
Charles Carmakal, CTO, Mandiant – Google Cloud, additionally confirmed that this was the flaw exploited by the Clop ransomware gang in information theft assaults that occurred in August 2025.
“Clop exploited a number of vulnerabilities in Oracle EBS which enabled them to steal massive quantities of knowledge from a number of sufferer in August 2025,” Carmakal shared in an announcement to BleepingComputer.
“A number of vulnerabilities have been exploited together with vulnerabilities that have been patched in Oracle’s July 2025 replace in addition to one which was patched this weekend (CVE-2025-61882),” continued Carmakal.
CVE-2025-61882 is a vital (9.8 CVSS) vulnerability that permits unauthenticated distant code execution.
Information of Clop’s newest extortion marketing campaign first broke final week, when Mandiant and the Google Risk Intelligence Group (GTIG) reported that they have been monitoring a brand new marketing campaign during which a number of corporations acquired emails claiming to be from the risk actors.
These emails said that Clop had stolen information from the corporate’s Oracle E-Enterprise Suite methods and have been demanding a ransom to not leak the stolen information.
“We’re CL0P staff. If you have not heard about us, you’ll be able to google about us on web,” reads the extortion e-mail shared with BleepingComputer.
“We’ve not too long ago breached your Oracle E-Enterprise Suite software and copied quite a lot of paperwork. All of the personal information and different info at the moment are held on our methods.”
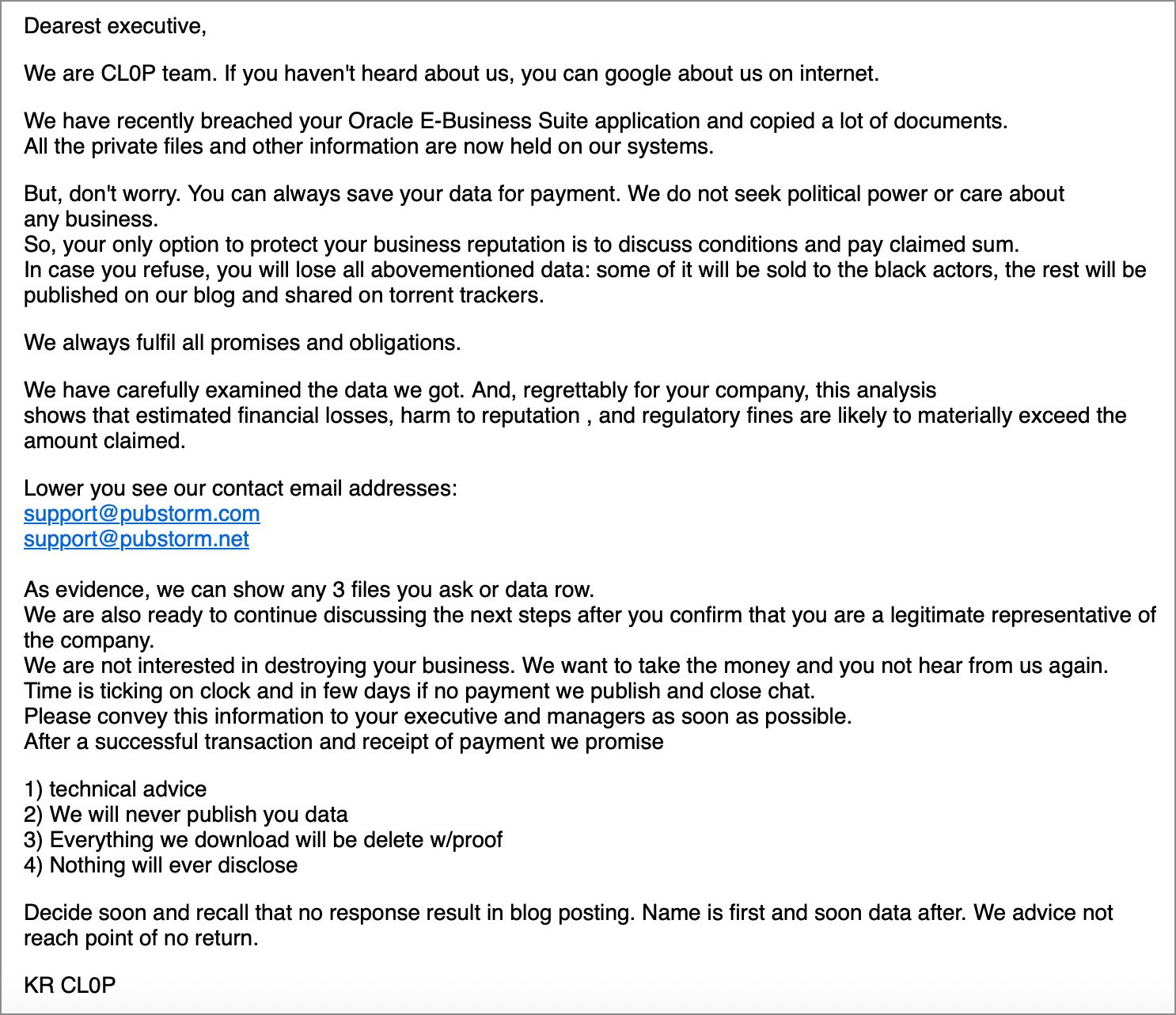
Supply: Google
The Clop extortion gang has an extended historical past of exploiting zero-day vulnerability in huge information theft assaults, which embrace:
Clop later confirmed to BleepingComputer that they have been behind the extortion emails and indicated they exploited an Oracle zero-day vulnerability to steal the information.
“Quickly all will turn out to be apparent that Oracle bugged up their core product and as soon as once more, the job is on clop to save lots of the day,” Clop informed BleepingComputer, indicating a brand new flaw was exploited.
Nonetheless, Oracle initially linked the Clop extortion marketing campaign to vulnerabilities that have been patched in July 2025 slightly than the brand new zero-day that we now know was used within the assaults.
Oracle has now shared indicators of compromise for the zero-day exploitation, which embrace two IP addresses seen exploiting servers, a command to open a distant shell, and the exploit archive and related information.
Exploit leaked by Scattered Lapsus$ Hunters
Whereas Clop is behind the information theft assaults and exploitation of the Oracle zero-day, information of the zero-day first got here from a distinct group of risk actors who’ve been making their very own headlines currently with their widespread information theft assaults on Salesforce prospects.
On Friday, these actors, calling themselves “Scattered Lapsus$ Hunters” as they declare to encompass risk actors from Scattered Spider, Lapsus$, and ShinyHunters, leaked two information on Telegram that they mentioned have been associated to the Clop assaults.
One file named “GIFT_FROM_CL0P.7z” incorporates Oracle supply code that seems to be associated to “assist.oracle.com” primarily based on the file names.
Nonetheless, the risk actors additionally launched an “ORACLE_EBS_NDAY_EXPLOIT_POC_SCATTERED_LAPSUS_RETARD_CL0P_HUNTERS.zip” archive, which they insinuated by the filename was the Oracle E-Enterprise exploit utilized by Clop.
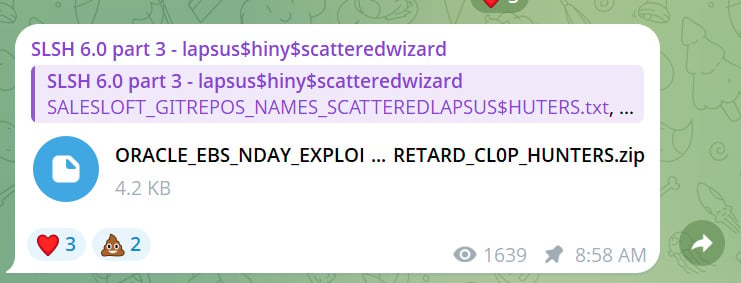
BleepingComputer has confirmed this is identical file listed in Oracle’s indicators of compromise.
This archives incorporates a readme.md instruction file and two Python scripts named exp.py and server.py. These Python scripts are used to take advantage of a susceptible Oracle E-Enterprise Suite occasion and both execute an arbitrary command or open a reverse shell again to the risk actor’s servers.
Because the IOCs shared by Oracle record the title of the exploit archive shared by Scattered Lapsus$ Hunters, it’s now confirmed that that is the exploit utilized by the Clop ransomware gang.
Nonetheless, it does increase questions on how the Scattered Lapsus$ Hunters risk actors gained entry to the exploit and whether or not they’re working with Clop in some capability.
BleepingComputer contacted representatives from each ShinyHunters and Clop to ask questions on this relationship, however has not acquired a response right now.


