
Microsoft plans to boost the safety of the Entra ID authentication system in opposition to exterior script injection assaults beginning in mid-to-late October 2026.
This replace will implement a strengthened Content material Safety Coverage that permits script downloads solely from Microsoft-trusted content material supply community domains and inline script execution solely from Microsoft-trusted sources throughout sign-ins.
After rollout, it is going to shield customers in opposition to numerous safety dangers, together with cross-site scripting assaults by which attackers inject malicious code into web sites to steal credentials or compromise techniques.
The replace coverage will apply solely to browser-based sign-in experiences at URLs starting with login.microsoftonline.com, and Microsoft Entra Exterior ID won’t be affected.
“This replace strengthens safety and provides an additional layer of safety by permitting solely scripts from trusted Microsoft domains to run throughout authentication, blocking unauthorized or injected code from executing in the course of the sign-in expertise,” mentioned Megna Kokkalera, product supervisor for Microsoft Id and Authentication Experiences.
Microsoft urged organizations to check sign-in eventualities earlier than the October 2026 deadline to establish and handle any dependencies on code-injection instruments.
IT directors can establish potential impression by reviewing sign-in flows within the browser developer console: violations will seem in crimson textual content with particulars in regards to the blocked scripts.
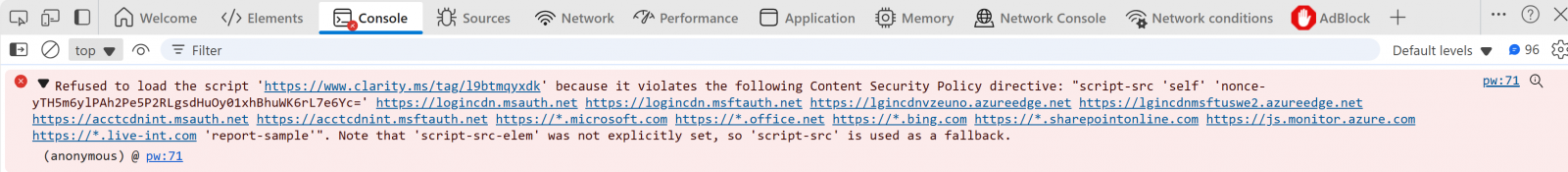
Microsoft additionally suggested enterprise prospects to cease utilizing browser extensions and instruments that inject code or scripts into sign-in pages earlier than the change takes impact. These will now not be supported and can cease working, though customers will nonetheless be capable of check in.
“This replace to our Content material Safety Coverage provides an extra layer of safety by blocking unauthorized scripts, additional serving to safeguard your group in opposition to evolving safety threats,” Kokkalera added.
This transfer is a part of Microsoft’s Safe Future Initiative (SFI), a company-wide effort launched two years in the past, in November 2023, following a report from the Cyber Security Assessment Board of the U.S. Division of Homeland Safety, which discovered that the corporate’s safety tradition was “insufficient and requires an overhaul.”
As a part of the identical initiative, Microsoft additionally up to date Microsoft 365 safety defaults to dam entry to SharePoint, OneDrive, and Workplace information by way of legacy authentication protocols, disabled all ActiveX controls in Home windows variations of Microsoft 365 and Workplace 2024 apps.
Earlier this month, it additionally started rolling out a brand new Groups function introduced in Could and designed to block display screen seize makes an attempt throughout conferences.



