
A brand new malicious marketing campaign is concentrating on macOS builders with pretend Homebrew, LogMeIn, and TradingView platforms that ship infostealing malware like AMOS (Atomic macOS Stealer) and Odyssey.
The marketing campaign employs “ClickFix” methods the place targets are tricked into executing instructions in Terminal, infecting themselves with malware.
Homebrew is a well-liked open-source bundle administration system that makes it simpler to put in software program on macOS and Linux. Risk actors have used previously the platform’s identify to distribute AMOS in malvertising campaigns.
LogMeIn is a distant entry service, and TradingView is a monetary charting and market evaluation platform, each extensively utilized by Apple customers.
Researchers at risk searching firm Hunt.io recognized greater than 85 domains impersonating the three platforms on this marketing campaign, together with the next:
| http://homebrewclubs.org/ | https://sites-phantom.com/ |
| http://homebrewfaq.org/ | https://tradingviewen.com/ |
| http://homebrewlub.us/ | https://tradingvieweu.com/ |
| http://homebrewonline.org/ | https://www.homebrewclubs.org/ |
| http://homebrewupdate.org/ | https://www.homebrewfaq.org/ |
| http://sites-phantom.com/ | https://www.homebrewfaq.us/ |
| http://tradingviewen.com/ | https://www.homebrewonline.org/ |
| http://tradingvieweu.com/ | https://www.homebrewupdate.org/ |
| http://www.homebrewfaq.us/ | https://www.tradingvieweu.com/ |
| http://www.homebrewonline.org/ | https://filmoraus.com/ |
| http://www.tradingviewen.com/ | https://homebrewfaq.org/ |
| https://filmoraus.com/ | https://homebrewfaq.us/ |
| https://homebrewfaq.org/ | https://homebrewlub.us/ |
When checking among the domains, BleepingComputer found that in some instances the visitors to the websites was pushed through Google Advertisements, indicating that the risk actor promoted them to seem in Google Search outcomes.
The malicious websites characteristic convincing obtain portals for the pretend apps and instruct customers to repeat a curl command of their Terminal to put in them, the researchers say.
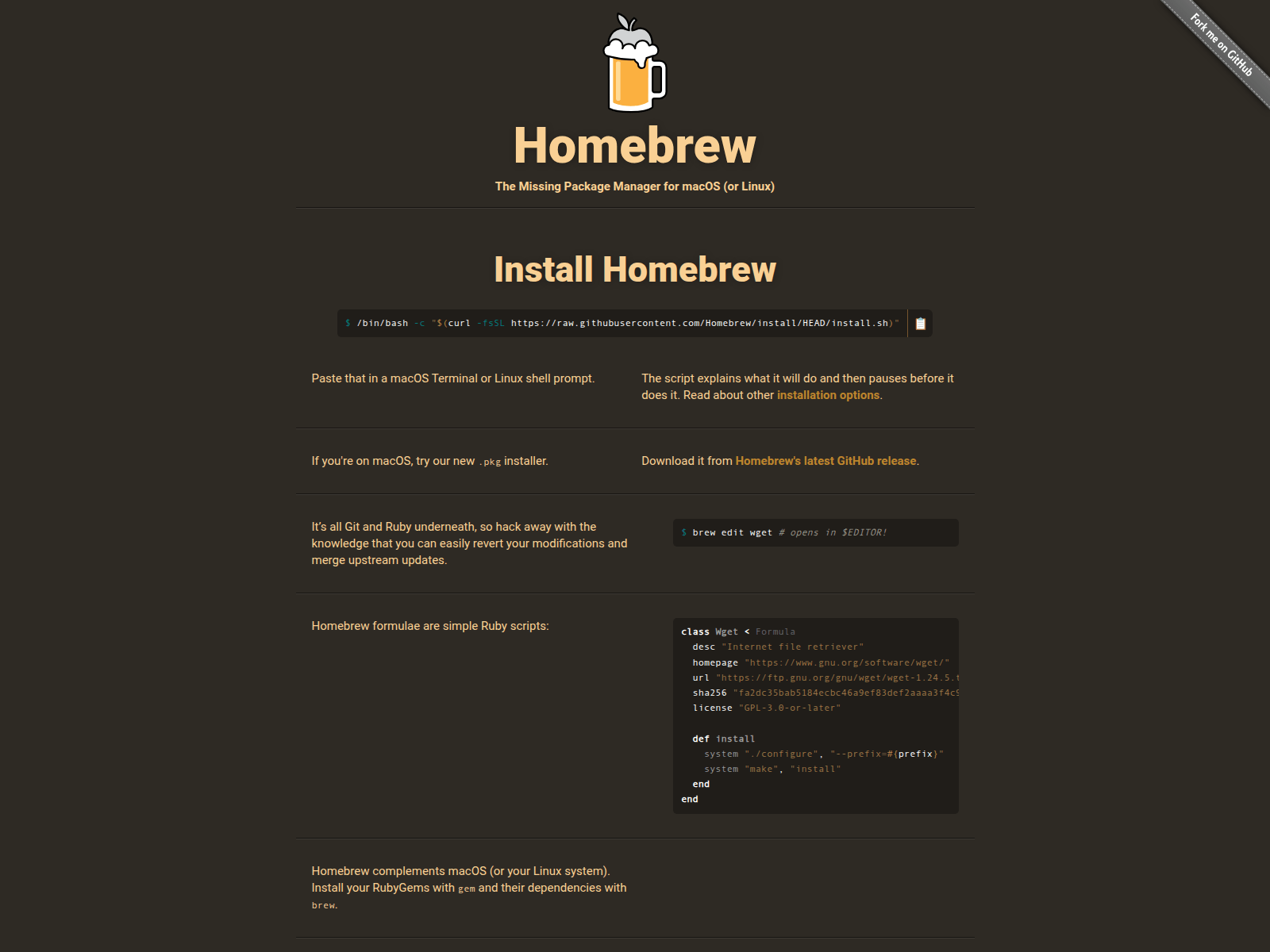
Supply: Hunt.io
In different instances, like for TradingView, the malicious instructions are introduced as a “connection safety affirmation step.” Nevertheless, if the person clicks on the ‘copy’ button, a base64-encoded set up command is delivered to the clipboard as an alternative of the displayed Cloudflare verification ID.
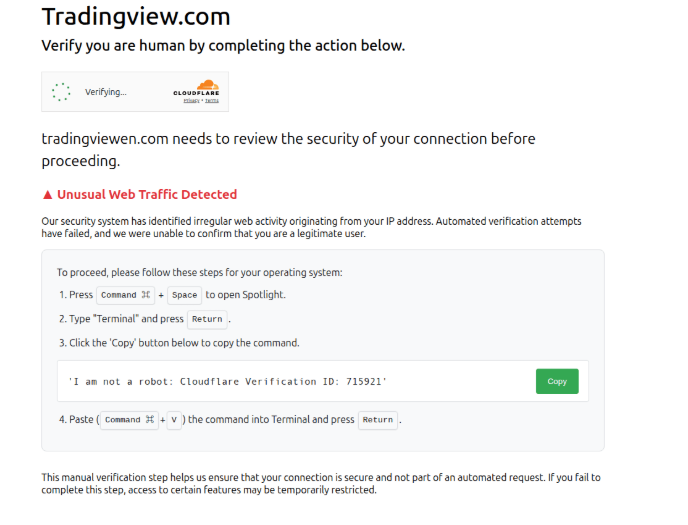
Supply: Hunt.io
The instructions fetch and decode an ‘set up.sh’ file, which downloads a payload binary, eradicating quarantine flags an bypass Gatekeeper prompts to permit its execution.
The payload is both AMOS or Odyssey, executed on the machine after checking if the surroundings is a digital machine or an evaluation system.
The malware explicitly invokes sudo to run instructions as root, and its first motion is to gather detailed {hardware} and reminiscence data of the host.
Subsequent, it manipulates system providers like killing OneDrive updater daemons and interacts with macOS XPC providers to mix its malicious exercise with official processes.
Finally, the information-stealing parts of the malware are activated, harvesting delicate data saved on the browser, cryptocurrency credentials, and exfiltrating to the command and management (C2).
AMOS, first documented in April 2023, is a malware-as-a-service (MaaS) accessible beneath a $1,000/month subscription. It could actually steal a broad vary of information from contaminated hosts.
Just lately, its creators added a backdoor part to the malware to offer operators distant persistent entry capabilities.
Odyssey Stealer, documented by CYFIRMA researchers this summer season, is a comparatively new household derived from the Poseidon Stealer, which itself was forked from AMOS.
It targets credentials and cookies saved in Chrome, Firefox, and Safari browsers, over 100 cryptocurrency pockets extensions, Keychain knowledge, and private recordsdata, and sends them to the attackers in ZIP format.
It’s strongly beneficial that customers do not paste within the Terminal instructions discovered on-line in the event that they don’t absolutely perceive what they do.


