
A extreme vulnerability affecting a number of MongoDB variations, dubbed MongoBleed (CVE-2025-14847), is being actively exploited within the wild, with over 80,000 doubtlessly susceptible servers uncovered on the general public net.
A public exploit and accompanying technical particulars can be found, exhibiting how attackers can set off the flaw to remotely extract secrets and techniques, credentials, and different delicate information from an uncovered MongoDB server.
The vulnerability was assigned a severity rating of 8.7 and has been dealt with as a “essential repair,” with a patch accessible for self-hosting cases since December 19.
Exploit leaks secrets and techniques
The MongoBleed vulnerability stems from how the MongoDB Server handles community packets processed by the zlib library for lossless information compression.
Researchers at Ox Safety clarify that the difficulty is brought on by MongoDB returning the quantity of allotted reminiscence when processing community messages as a substitute of the size of the decompressed information.
A menace actor might ship a malformed message claiming a bigger dimension when decompressed, inflicting the server to allocate a bigger reminiscence buffer and leak to the shopper in-memory information with delicate data.
The kind of secrets and techniques leaked this fashion might vary from credentials, API and/or cloud keys, session tokens, personally identifiable information (PII), inner logs, configurations, paths, and client-related information.
As a result of the decompression of community messages happens earlier than the authentication stage, an attacker exploiting MongoBleed doesn’t want legitimate credentials.
The general public exploit, launched as a proof-of-concept (PoC) dubbed “MongoBleed” by Elastic safety researcher Joe Desimone, is particularly created to leak delicate reminiscence information.
Safety researcher Kevin Beaumont says that the PoC exploit code is legitimate and that it requires solely “an IP deal with of a MongoDB occasion to begin ferreting out in reminiscence issues akin to database passwords (that are plain textual content), AWS secret keys and many others.”
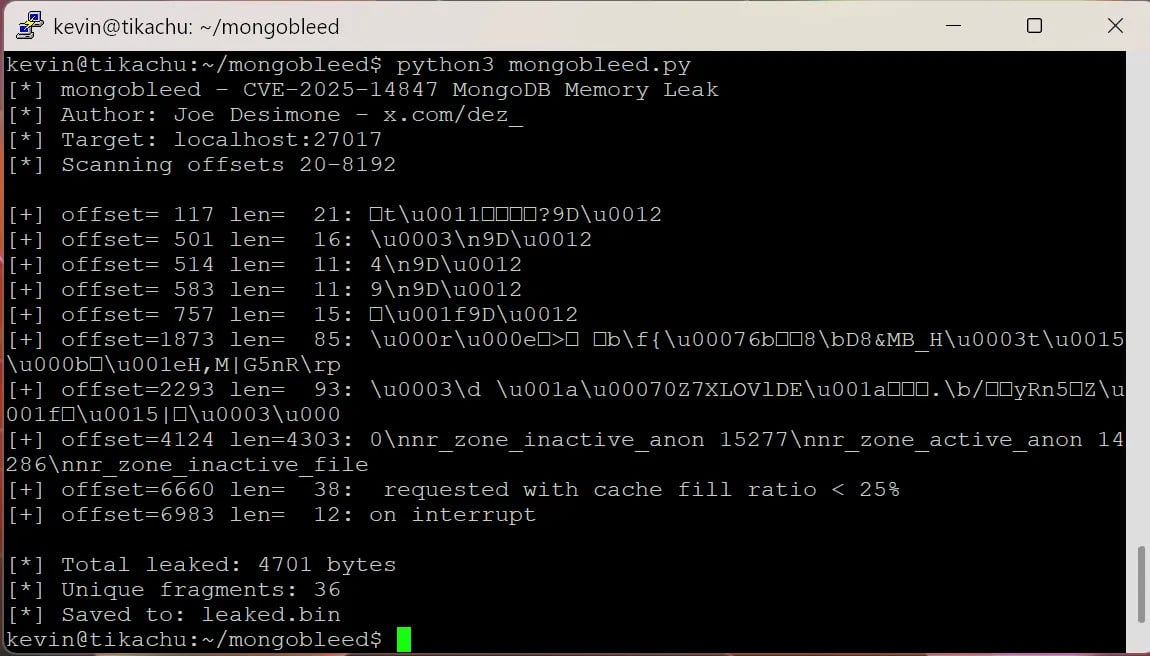
supply: Kevin Beaumont
In keeping with the Censys platform for locating internet-connected units, as of December 27, there have been greater than 87,000 doubtlessly susceptible MongoDB cases uncovered on the general public web.
Nearly 20,000 MongoDB servers had been noticed in the USA, adopted by China with virtually 17,000, and Germany with just a little beneath 8,000.
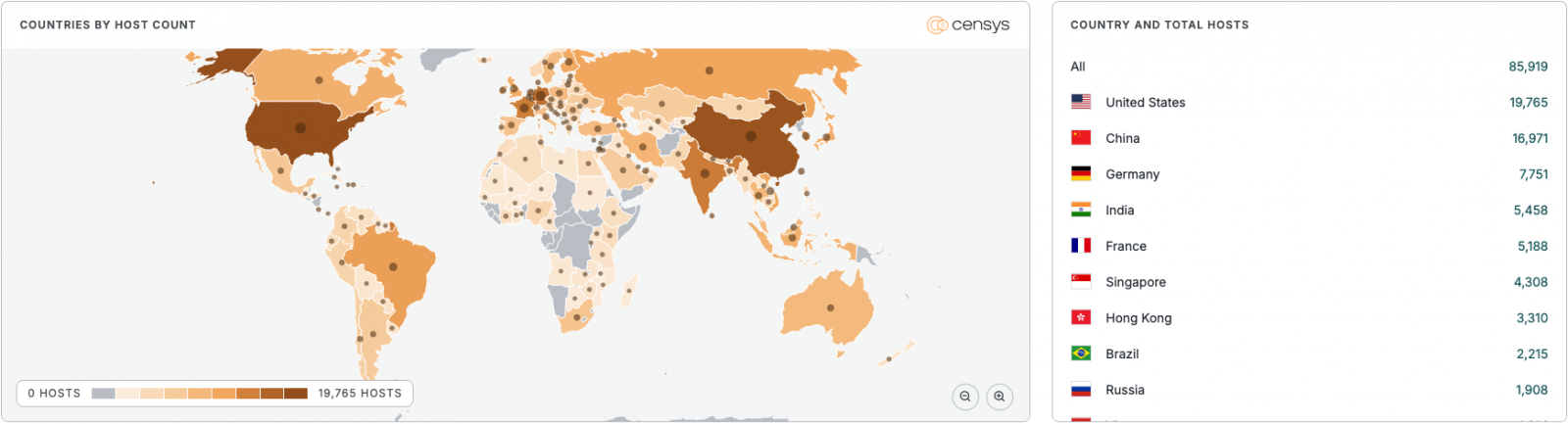
supply: Censys
Exploitation and detection
The impression throughout the cloud atmosphere additionally seems to be important, as telemetry information from cloud safety platform Wiz confirmed that 42% of the seen methods “have at the least one occasion of MongoDB in a model susceptible to CVE-2025-14847.”
Wiz researchers notice that the cases they noticed included each inner sources and publicly uncovered ones. The corporate says that it noticed MongoBleed (CVE-2025-14847) exploitation within the wild, and recommends organizations prioritize patching.
Whereas unverified, some menace actors are claiming to have used the MongoBleed flaw in a latest of breach of Ubisoft’s Ranbow Six Siege on-line platform.
Recon InfoSec co-founder Eric Capuano warns that patching is simply a part of the response to the MongoBleed downside and advises organizations to additionally verify for indicators of compromise.
In a weblog submit yesterday, the researcher explains a detection technique that features trying for “a supply IP with a whole lot or hundreds of connections however zero metadata occasions.”
Nonetheless, Capuano warns that the detection relies on the presently accessible proof-of-concept exploit code and that an attacker might modify it to incorporate faux shopper metadata or scale back exploitation pace.
Florian Roth – the creator of the THOR APT Scanner and hundreds of YARA rules- utilized Capuano’s analysis to create the MongoBleed Detector – a device that parses MongoDB logs and identifies potential exploitation of the CVE-2025-14847 vulnerability.
Secure lossless compression instruments
MongoDB addressed the MongoBleed vulnerability ten days in the past, with a powerful suggestion for directors to improve to a secure launch (8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, or 4.4.30).
The seller is warning that a big record of MongoDB variations are impacted by MongoBleed (CVE-2025-14847), some legacy variations launched as early as late 2017, and a few as latest as November 2025:
- MongoDB 8.2.0 by 8.2.3
- MongoDB 8.0.0 by 8.0.16
- MongoDB 7.0.0 by 7.0.26
- MongoDB 6.0.0 by 6.0.26
- MongoDB 5.0.0 by 5.0.31
- MongoDB 4.4.0 by 4.4.29
- All MongoDB Server v4.2 variations
- All MongoDB Server v4.0 variations
- All MongoDB Server v3.6 variations
Prospects of MongoDB Atlas, the absolutely managed, multi-cloud database service, obtained the patch routinely and don’t must take any motion.
MongoDB says that there isn’t any workaround for the vulnerability. If shifting to a brand new model will not be attainable, the seller recommends that clients disable zlib compression on the server and offers directions on how to take action.
Secure options for lossless information compression embrace Zstandard (zstd) and Snappy (previously Zippy), maintained by Meta and Google, respectively.
Damaged IAM is not simply an IT downside – the impression ripples throughout your entire enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM seems like, and a easy guidelines for constructing a scalable technique.



