
Cybercriminals are more and more abusing the AI-powered Lovable web site creation and internet hosting platform to generate phishing pages, malware-dropping portals, and varied fraudulent web sites.
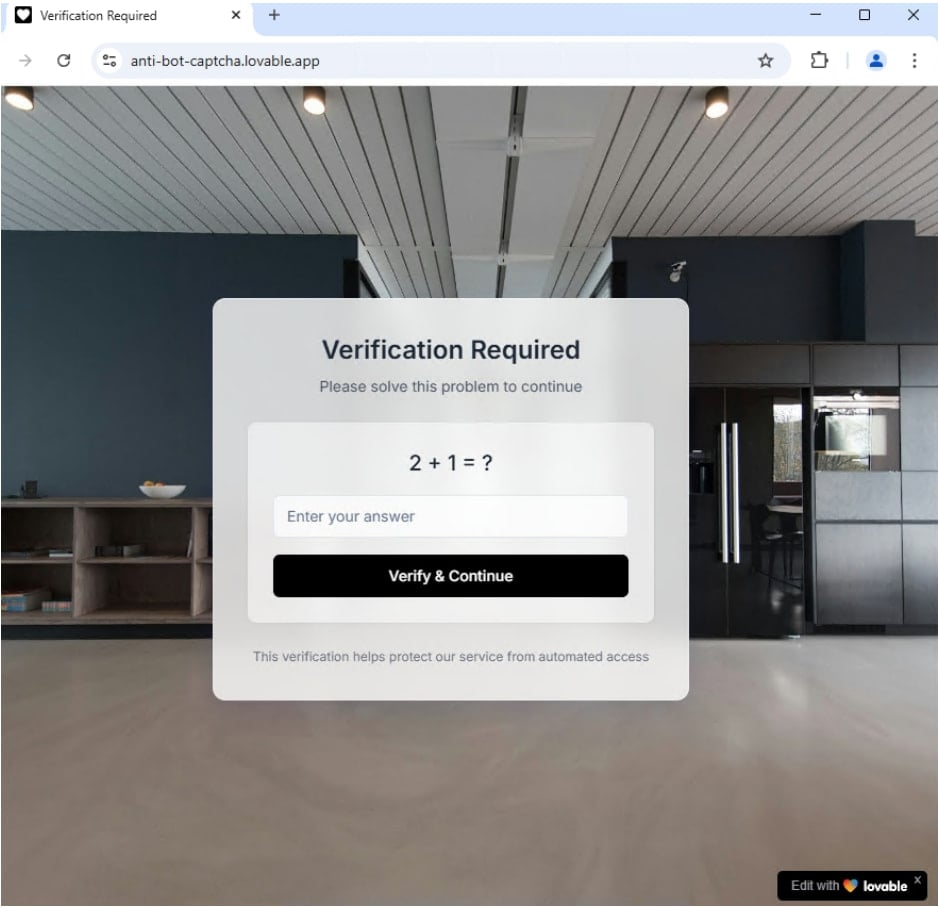
The malicious websites created by means of the platform impersonate massive and recognizable manufacturers, and have site visitors filtering methods like CAPTCHA to maintain bots out.
Whereas Lovable has taken steps to raised defend its platform from abuse, as AI-powered website mills enhance in quantity, the barrier to coming into cybercrime continues to drop.
Supply: Proofpoint
Lovable-powered campaigns
Since February, cybersecurity firm Proofpoint “noticed tens of hundreds of Lovable URLs” that had been delivered in e mail messages and had been flagged as threats.
In a report as we speak, the researchers describe 4 malicious campaigns that abused the Lovable AI web site builder.
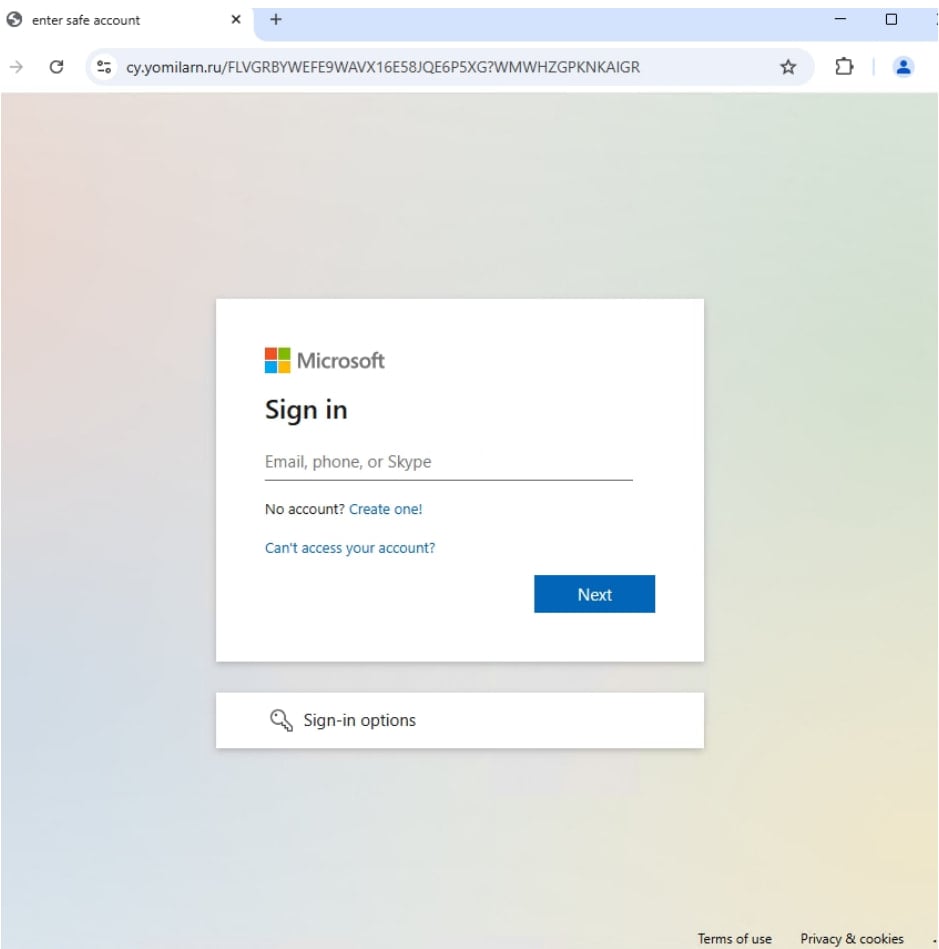
One instance is a large-scale operation that relied on the phishing-as-a-service platform generally known as Tycoon. Emails contained Lovable-hosted hyperlinks that opened with a CAPTCHA after which redirected customers to pretend Microsoft login pages that includes Azure AD or Okta branding.
These websites harvested person credentials, multi-factor authentication (MFA) tokens, and session cookies by means of adversary-in-the-middle strategies. Throughout the campaigns, the risk actor despatched a whole bunch of hundreds of messages to five,000 organizations.
Supply: Proofpoint
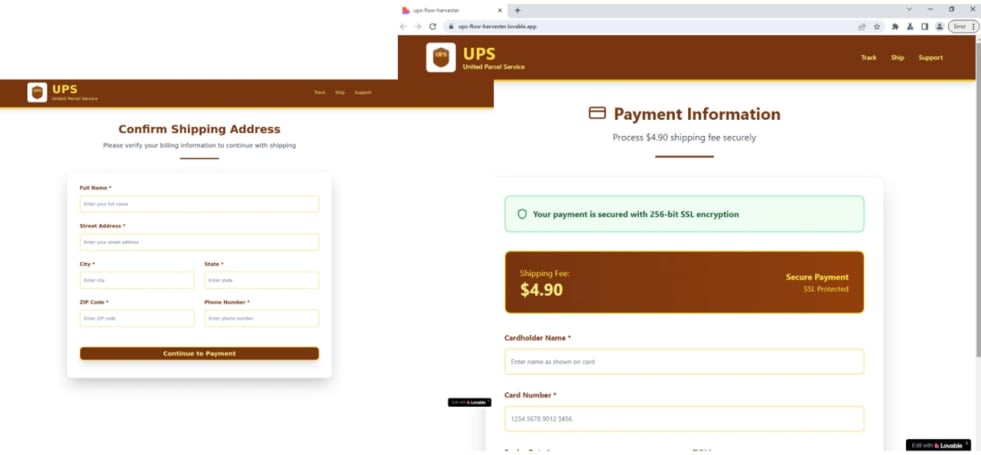
A second instance was a cost and knowledge theft marketing campaign that impersonated UPS, sending almost 3,500 phishing emails with hyperlinks that directed victims to phishing websites.
The websites requested guests to enter private particulars, bank card numbers, and SMS codes, which had been then despatched to a Telegram channel managed by the attacker.
Supply: Proofpoint
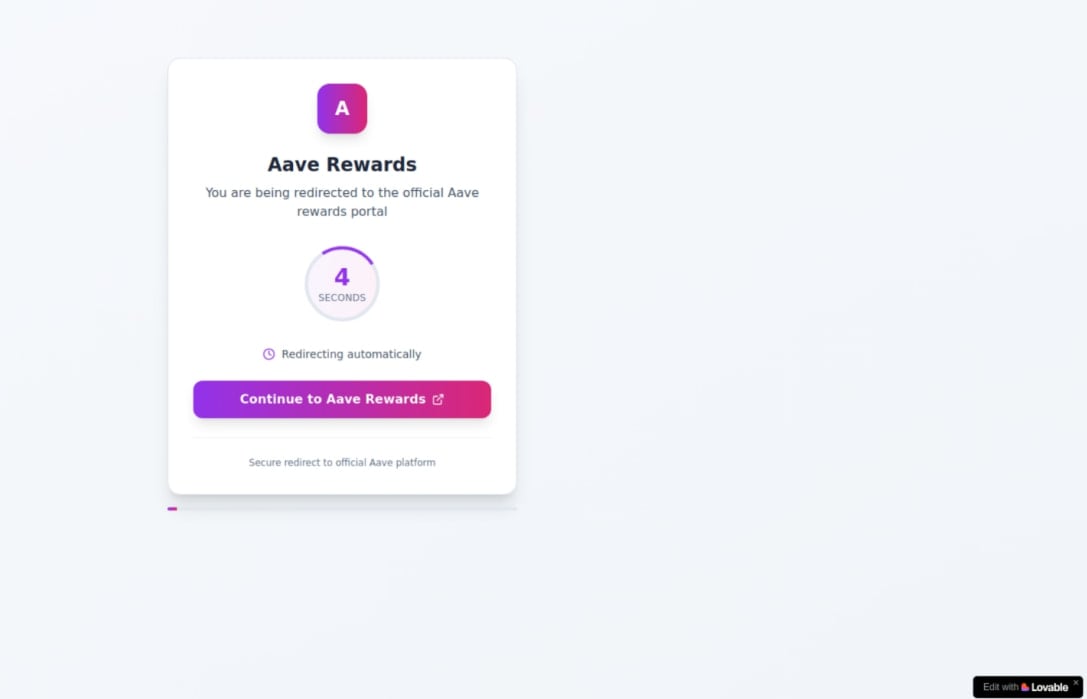
The third is a cryptocurrency theft marketing campaign that impersonated the DeFi platform Aave, sending out near 10,000 emails by way of SendGrid.
Focused customers had been led to Lovable-generated redirects and phishing pages designed to trick them into connecting their wallets, possible adopted by asset drainage.
Supply: Proofpoint
The fourth case issues a malware supply marketing campaign distributing the distant entry trojan zgRAT.
Emails contained hyperlinks that led to Lovable apps posing as bill portals, which delivered RAR archives hosted on Dropbox.
The information included a respectable signed executable alongside a trojanized DLL that launched DOILoader, finally loading zgRAT.
Responding to the abuse
Lovable launched real-time detection of malicious website creation in July, and likewise robotically scans revealed tasks every day to identify and delete any fraud makes an attempt.
The developer additionally said that it plans to introduce further protections this fall, which might proactively establish and block abusive accounts on the platform.
Guardio Labs confirmed to BleepingComputer that Lovable can nonetheless be used to create malicious websites. In a latest take a look at, the researchers generated a fraudulent website to impersonate a big retailer and encountered no objection from the platform.
BleepingComputer has contacted Lovable to ask concerning the effectiveness of the present anti-abuse measures on the platform, however a remark wasn’t instantly out there.


