
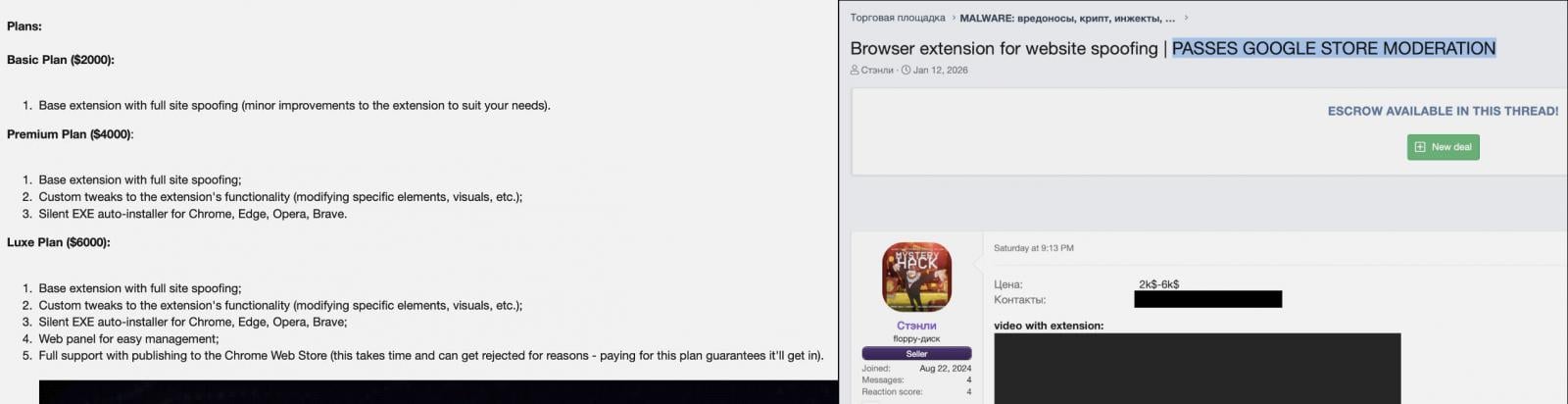
A brand new malware-as-a-service (MaaS) known as ‘Stanley’ guarantees malicious Chrome extensions that may clear Google’s assessment course of and publish them to the Chrome Net Retailer.
Researchers at end-to-end knowledge safety firm Varonis named the mission Stanley after the alias of the vendor, who advertises straightforward phishing assaults by intercepting navigation and overlaying a webpage with an iframe with content material of the attacker’s alternative.
The brand new MaaS providing is for malicious Chrome extensions that may cowl a webpage with a full-screen iframe containing phishing content material of the attacker’s alternative. Stanley additionally advertises silent auto-installation on Chrome, Edge, and Courageous browsers and help for customized tweaks.
The MaaS has a number of subscription tiers, the most costly one being the Luxe Plan, which additionally provides an online panel and full help for publishing the malicious extension to the Chrome Net Retailer.
Supply: Varonis
BleepingComputer has contacted Google to request a touch upon these claims, and we’ll replace this put up after we hear again.
Varonis reviews that Stanley works by overlaying a full-screen iframe with malicious content material whereas the sufferer’s browser handle bar stays untouched, displaying the legit area.
.jpg)
Supply: Varonis
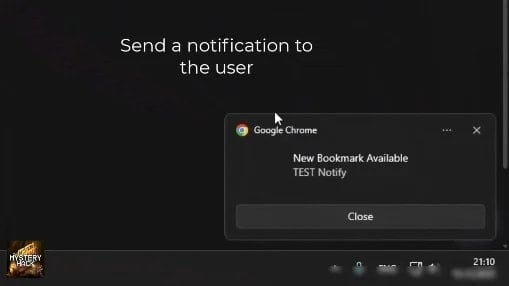
Operators who’ve entry to Stanley’s panel can allow or disable hijacking guidelines on demand, and even push notifications straight within the sufferer’s browser to lure them to particular pages, pushing the phishing course of extra aggressively.
Supply: Varonis
Stanley helps IP-based sufferer identification and permits geographic concentrating on and correlation throughout classes and units.
Furthermore, the malicious extension performs persistent command-and-control (C2) polling each 10 seconds, and it will probably additionally carry out backup area rotation to supply resilience in opposition to takedowns.
Varonis feedback that, from a technical perspective, Stanley lacks superior options and as an alternative opts for a simple strategy to implementing well-known methods.
Its code is reportedly “tough” at locations, that includes Russian feedback, empty catch blocks, and inconsistent error dealing with.
What actually makes this new MaaS stand out is its distribution mannequin, particularly the promise to cross the Chrome Net Retailer assessment and get malicious extensions onto the biggest platform of trusted browser add-ons.
On condition that such extensions proceed to slide by way of the cracks, as lately highlighted in two separate reviews by Symantec and LayerX, customers ought to set up solely the minimal variety of extensions they want, learn consumer opinions, and ensure the writer’s trustworthiness.



