
North Korean hackers are abusing Google’s Discover Hub device to trace the GPS location of their targets and remotely reset Android gadgets to manufacturing unit settings.
The assaults are primarily concentrating on South Koreans, and begin by approaching the potential victims over KakaoTalk messenger – the most well-liked prompt messaging app within the nation.
South Korean cybersecurity options firm Genians hyperlinks the malicious exercise to a KONNI exercise cluster, which “has overlapping targets and infrastructure with Kimsuky and APT37.”
KONNI usually refers to a distant entry device that has been linked to assaults from North Korean hackers within the APT37 (ScarCruft) and Kimsuky (Emerald Sleet) teams that focused a number of sectors (e.g., schooling, authorities, and cryptocurrency).
In response to Genians, the KONNI marketing campaign infects computer systems with distant entry trojans that allow delicate information exfiltration.
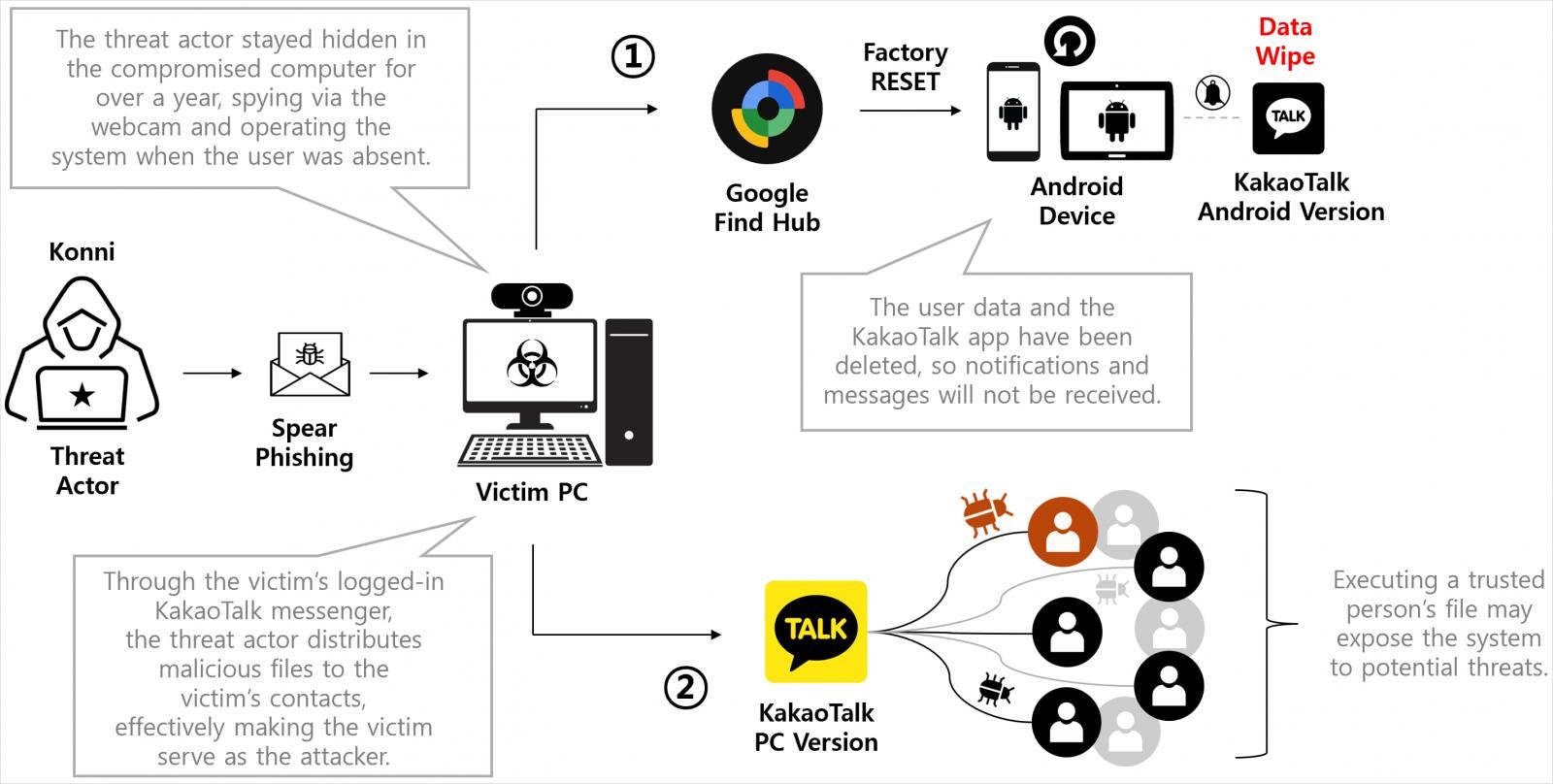
Wiping Android gadgets is completed to isolate victims, delete assault traces, delay restoration, and silence safety alerts. Particularly, the reset disconnects victims from KakaoTalk PC periods, which the attackers hijack post-wiping to unfold to their targets’ contacts.
An infection chain
The KONNI marketing campaign analyzed by Genians targets victims by way of spear-phishing messages that spoof South Korea’s Nationwide Tax Service, the police, and different companies.
As soon as the sufferer executes the digitally signed MSI attachment (or a .ZIP containing it), the file invokes an embedded set up.bat and an error.vbs script used as a decoy to mislead the consumer with a pretend “language pack error.”
The BAT triggers an AutoIT script (IoKITr.au3) that units persistence on the machine by way of a scheduled process. The script fetches extra modules from a command and management (C2) level, and gives the risk actors with distant entry, keylogging, and extra payload introduction capabilities.
Genians experiences that the secondary payloads retrieved by the script embrace RemcosRAT, QuasarRAT, and RftRAT.
These instruments are used for harvesting the sufferer’s Google and Naver account credentials, which allows them to log into the targets’ Gmail and Naver mail, change safety settings, and wipe logs exhibiting compromise.
Utilizing Discover Hub to reset gadgets
From the compromised Google account, the attacker opens Google Discover Hub to retrieve registered Android gadgets and question their GPS location.
Discover Hub is Android’s default “Discover my System” device, permitting customers to remotely find, lock, and even wipe Android gadgets in circumstances of loss or theft.
Genians’ forensic evaluation of a number of sufferer pc programs revealed that the attacker wiped a goal’s machine via Discover Hub’s distant reset command.
“The investigation discovered that on the morning of September 5 a risk actor compromised and abused the KakaoTalk account of a South Korea–based mostly counselor who makes a speciality of psychological assist for North Korean defector youth, and despatched a malicious file disguised as a “stress aid program” to an precise defector pupil,” Genians researchers say.
The researchers say that the hackers used the GPS monitoring characteristic to pick out a time when their goal was outdoors and fewer able to urgently responding to the state of affairs.
Supply: Genians Safety
Throughout the assault, the risk actor ran the distant reset instructions on all registered Android gadgets. This led to the entire deletion of essential information. The attacker executed the wipe instructions thrice, which prevented restoration and use of the gadgets for an extended interval.
With the cellular alerts neutralized, the attacker used the sufferer’s logged-in KakaoTalk PC session on the already compromised pc to distribute malicious information to the sufferer’s contacts.
On September 15, Genians seen one other assault on a separate sufferer utilizing the identical methodology.
To dam these assaults, it is strongly recommended to guard Google accounts by enabling multi-factor authentication and guaranteeing fast entry to a restoration account.
When receiving information on messenger apps, at all times attempt to confirm the sender’s identification by calling them instantly earlier than downloading/opening them.
Genians’ report features a technical evaluation of the malware used in addition to a listing of indicators of compromise (IoCs) associated to the investigated exercise.
Replace 11/11 – A Google spokesperson has despatched BleepingComputer the next remark relating to the above.
“This assault didn’t exploit any safety flaw in Android or Discover Hub. The report signifies this focused assault required PC malware to be current as a way to steal Google account credentials and abuse authentic capabilities in Discover Hub (previously Discover My System). We strongly urge all customers to allow 2-Step Verification or passkeys for complete safety towards credential theft. For customers going through greater visibility or focused assaults, we suggest enrolling in our Superior Safety Program for Google’s strongest stage of account safety.” – A Google spokesperson.



