
Risk actors are actively exploiting a vital vulnerability within the Service Finder WordPress theme that permits them to bypass authentication and log in as directors.
Administrator privileges in WordPress grant full management over content material and settings, permission to create accounts, add PHP recordsdata, and export databases.
WordPress plugin safety agency Wordfence recorded greater than 13,800 exploitation atempts since August 1st.
Service Finder is a premium WordPress theme designed for service listing and job board web sites. It helps buyer reserving, suggestions, time slot administration, workers administration, bill technology, and a cost system.
The theme has extra 6,000 gross sales on Envato Market, and like most premium plugins, it’s sometimes utilized by energetic websites.
The vulnerability exploited within the newest assaults is tracked as CVE-2025-5947 and has a vital severity rating of 9.8. It impacts Service Finder variations 6.0 and older, stemming from an improper validation of the original_user_id cookie within the service_finder_switch_back() operate.
An attacker exploiting CVE-2025-5947 can log in as any consumer, together with directors, with out authentication.
The difficulty was found by safety researcher ‘Foxyyy,’ who reported it by Wordfence’s bug bounty program on June 8.
Aonetheme, the theme’s vendor, addressed the safety challenge in model 6.1, launched on July 17. On the finish of the month, the difficulty was publicly disclosed and exploitation started the following day.
For a few week since September 23, Wordfence noticed a surge of greater than 1,500 assault makes an attempt daily. Total, the researchers noticed greater than 13,800 exploit makes an attempt.
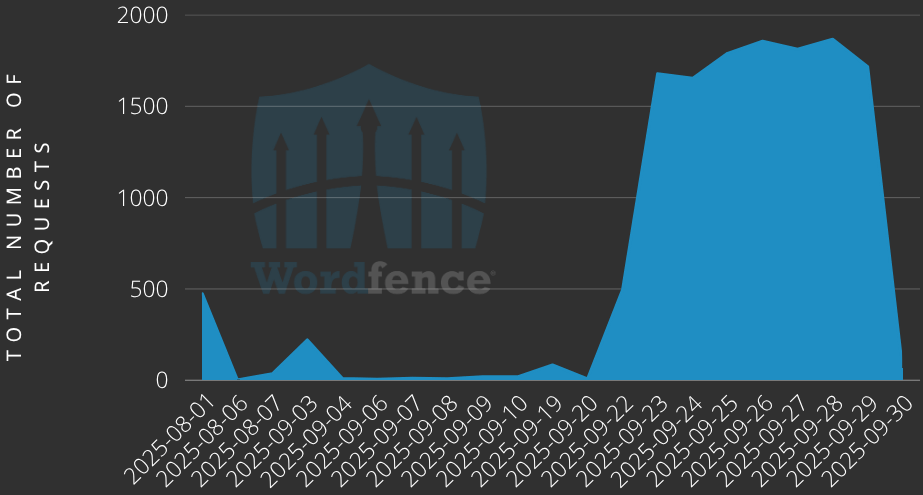
Supply: Wordfence
Primarily based on Wordfence’s observations, a typical assault contains an HTTP GET request to the foundation path with a question parameter (switch_back=1) to impersonate an current consumer.
The researchers say that there are a number of IP addresses used for launching the assaults. Nevertheless, 1000’s of assault requests orginated from simply 5 of them:
- 5.189.221.98
- 185.109.21.157
- 192.121.16.196
- 194.68.32.71
- 178.125.204.198
As a part of protection measures in opposition to these assaults is blocklisting the above IP addresses. Nevertheless, it must be famous that attackers can swap to new ones.
The researchers say that there aren’t any clear indicators of compromise to cease these assaults aside from requests that comprise the ‘switch_back’ parameter.
Web site directors ought to assessment all logs for suspicious exercise or accounts that menace actors might create for persistence.
Wordfence warns that “the absence of any such log entries doesn’t assure that your web site has not been compromised,” as administrator entry offers attackers the potential to cowl their tracks by deleting logs or different proof.
Given the energetic exploitation standing of CVE-2025-5947, customers of the Service Finder theme are really useful to use the safety replace as quickly as attainable or cease utilizing the plugin.


