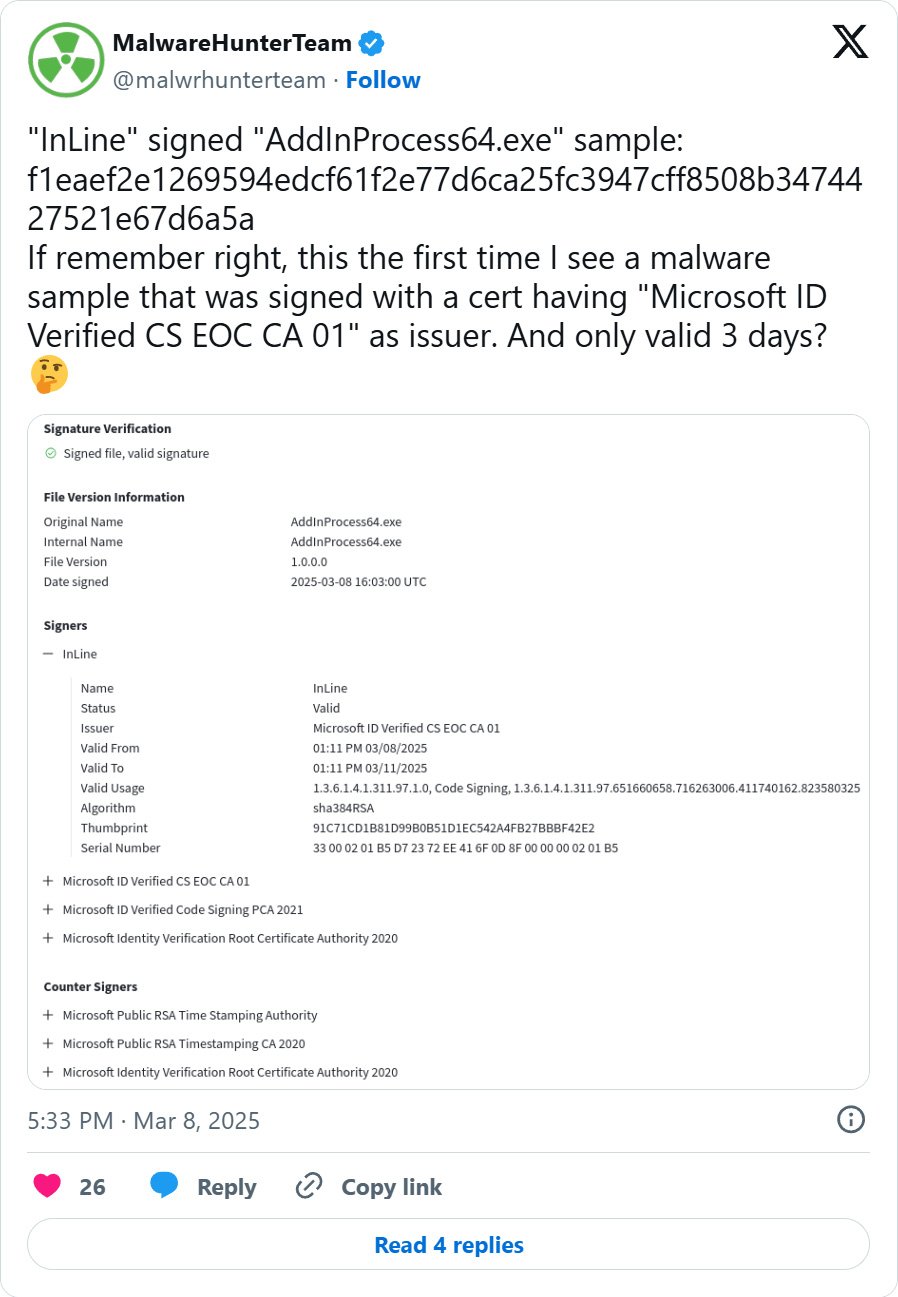
Cybercriminals are abusing Microsoft’s Trusted Signing platform to code-sign malware executables with short-lived three-day certificates.
Menace actors have lengthy wanted code-signing certificates as they can be utilized to signal malware to seem like they’re from a respectable firm.
Signed malware additionally has the benefit of probably bypassing safety filters that might usually block unsigned executables, or a minimum of deal with them with much less suspicion.
The holy grail for risk actors is to acquire Prolonged Validation (EV) code-signing certificates, as they routinely acquire elevated belief from many cybersecurity applications because of the extra rigorous verification course of. Much more necessary, EV certificates are believed to realize a status enhance in SmartScreen, serving to to bypass alerts that might usually be displayed for unknown recordsdata.
Nevertheless, EV code-singing certificates might be tough to acquire, requiring them to be stolen from different firms or for risk actors to arrange faux companies and spend hundreds of {dollars} to buy one. Moreover, as soon as the certificates is utilized in a malware marketing campaign, it’s normally revoked, making it unusable for future assaults.
Abusing Microsoft Trusted Signing service
Just lately, cybersecurity researchers have seen risk actors using the Microsoft Trusted Signing service to signal their malware with short-lived, three-day code-signing certificates.
These malware samples are signed by “Microsoft ID Verified CS EOC CA 01” and the certificates is simply legitimate for 3 days. Whereas the certificates expires three days after being issued, it is very important observe that executables signed with it’ll nonetheless be thought-about legitimate till the issuer revokes the certificates.
Since then different researchers and BleepingComputer have discovered quite a few different samples utilized in ongoing malware campaigns, together with these utilized in a Loopy Evil Traffers crypto-theft marketing campaign [VirusTotal] and Lumma Stealer [VirusTotal] campaigns.
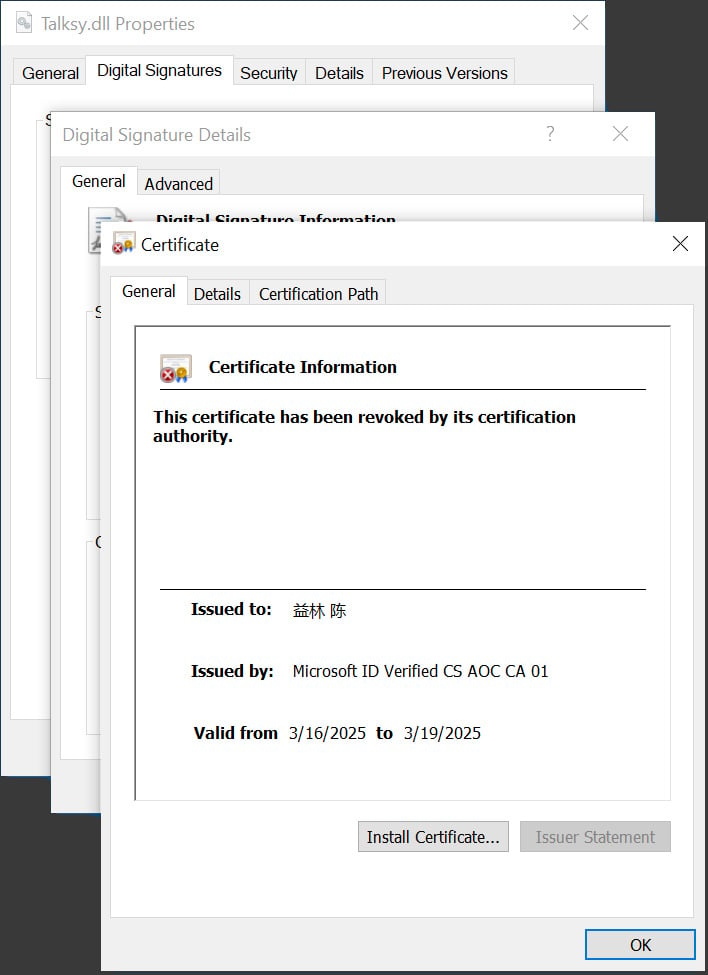
Supply: BleepingComputer
The Microsoft Trusted Signing service launched in 2024 and is a cloud-based service that enables builders to simply have their applications signed by Microsoft.
“Trusted Signing is a full code signing service with an intuitive expertise for builders and IT professionals, backed by a Microsoft managed certification authority,” reads a Microsoft announcement for the service.
“The service helps each private and non-private belief signing situations and features a timestamping service.”
The platform has a $9.99 month-to-month subscription service designed to make it simple for builders to signal their executables, whereas additionally providing further safety.
This elevated safety is completed through the use of short-lived certificates that may simply be revoked within the occasion of abuse and by by no means issuing the certificates on to the builders, stopping them from being stolen within the occasion of a breach.
Microsoft additionally says certificates issued by the Trusted Signing service present an analogous SmartScreen status enhance to executables signed by its service.
“A Trusted Signing signature ensures that your utility is trusted by offering base status on sensible display screen, person mode belief on Home windows, and integrity examine signature validation compliant,” reads an FAQ on the Trusted Signing web site.
To guard towards abuse, Microsoft is presently solely permitting certificates to be issued underneath an organization title if they’ve been in enterprise for 3 years.
Nevertheless, people can join and get authorized extra simply if they’re okay with the certificates being issued underneath their title.
An easier path
A cybersecurity researcher and developer often called ‘Squiblydoo,’ who has been monitoring malware campaigns abusing certificates for years, informed BleepingComputer that they consider risk actors are switching to Microsoft’s service out of comfort.
“I feel there are a couple of causes for the change. For a very long time, utilizing EV certificates has been the usual, however Microsoft has introduced modifications to EV certificates,” Squiblydoo informed BleepingComputer.
“Nevertheless, the modifications to EV certificates actually aren’t clear to anybody: not certificates suppliers, not attackers. Nevertheless, because of these potential modifications and lack of readability, simply having a code-signing certificates could also be ample for attacker wants.”
“On this regard, the verification course of for Microsoft’s certificates is considerably simpler than the verification course of for EV certificates: because of the ambiguity over EV certificates, it is sensible to make use of the Microsoft certificates.”
BleepingComputer contacted Microsoft concerning the abuse and was informed that the corporate makes use of risk intelligence monitoring to search out and revoke certificates as they’re discovered.
“We use lively risk intelligence monitoring to continually search for any misuse or abuse of our signing service,” Microsoft informed BleepingComputer.
“After we detect threats we instantly mitigate with actions resembling broad certificates revocation and account suspension. The malware samples you shared are detected by our antimalware merchandise and we’ve already taken motion to revoke the certificates and stop additional account abuse.”